The Silent Payroll Heist Hitting Universities
As campuses gear up for another academic year, a quieter — but equally damaging — threat is draining university budgets: direct deposit fraud.
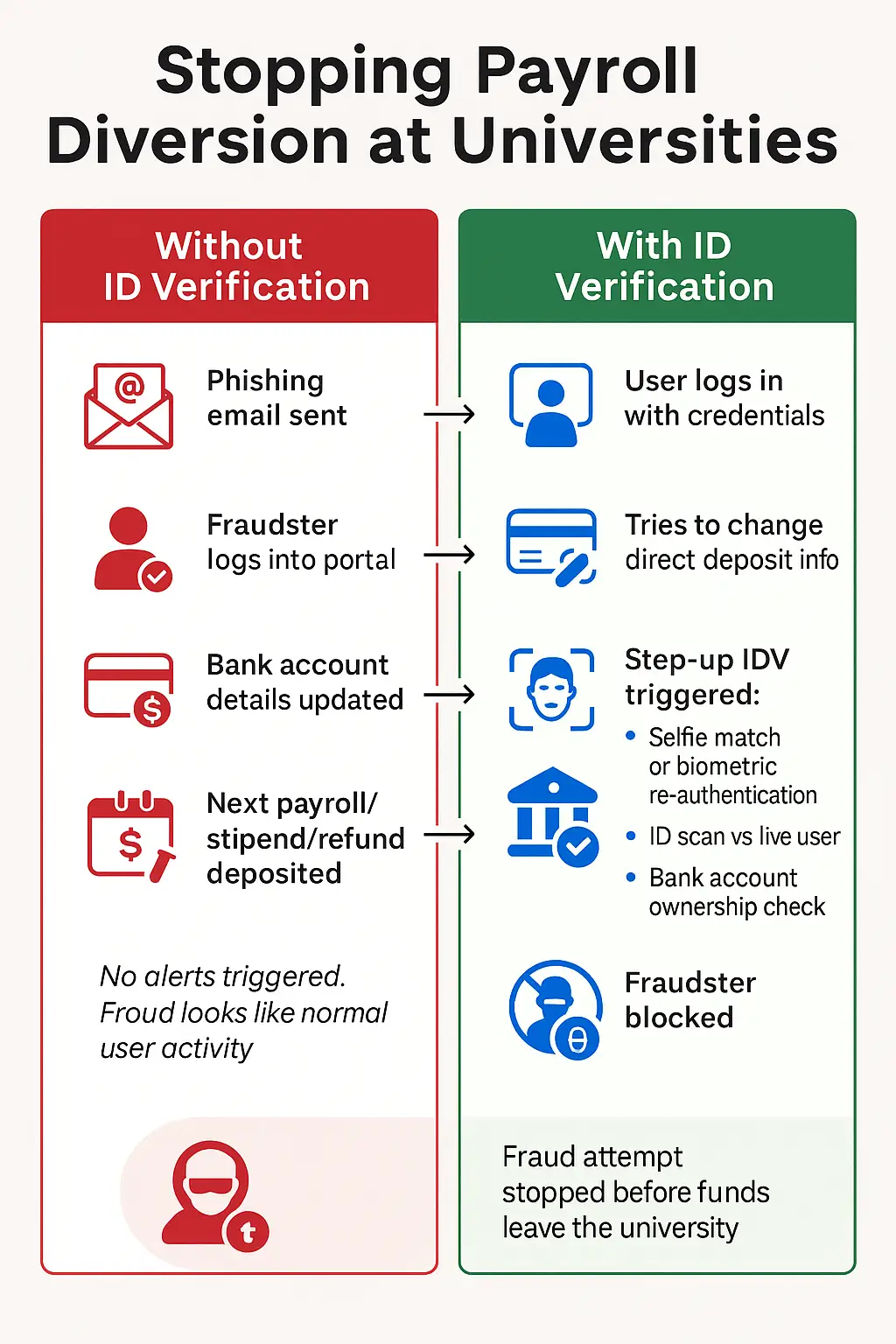
This isn’t ransomware that makes headlines by shutting down networks. Instead, it slips through unnoticed. Fraudsters steal credentials, log in like a legitimate user, and quietly reroute paychecks, stipends, and refunds to their own accounts. By the time faculty or students realize a payment is missing, the money is long gone.
Why Universities Are Prime Targets
Universities process millions in payments every semester:
- Faculty and staff payroll
- Student worker wages
- Research and graduate stipends
- Tuition refunds and financial aid
The attack surface is huge. Thousands of new students and employees join each term, many with limited cybersecurity awareness. Add in multiple disconnected systems (HR, payroll, bursar) and self-service portals that let users update bank info with little verification, and it’s a fraudster’s dream.
Anatomy of a Campus Heist
The playbook is simple:
- Compromise credentials – via phishing or stolen logins.
- Access payroll/portal – log in as the user.
- Change direct deposit info – update bank details to a mule account.
- Wait for payday – the next paycheck or refund flows to the fraudster.
- No malware. No alarms. Just stolen wages.
The True Cost
Beyond the missing funds, universities are left scrambling:
- Covering replacement paychecks
- Hours of admin and IT investigation
- Damaged credit and financial stress for victims
- Reputational hits that erode trust with faculty and students
Worse, once a fraudster succeeds at one campus, the same playbook spreads quickly to others.
The Identity Gap
The weakness isn’t the technology — it’s the assumption. Most systems trust that if you know the password, you must be the rightful owner. In today’s world of credential compromise, that assumption is broken.
How to Stop It: Three Layers of Protection
Universities can close the gap by verifying more than just passwords:
- Verify the person
- Step-up identity checks at the moment of a bank account change — government ID scan + selfie match, or biometric re-authentication.
- Verify the account
- Use services like Plaid to confirm the bank account is actually owned by the verified user, not a money mule.
- Verify the risk
- Apply risk-based rules: if the request comes from a new device or unusual location, enforce stronger checks before approving changes.
Together, these controls stop fraudsters cold, even if they’ve stolen valid credentials.
The Path Forward
Direct deposit fraud may not make headlines, but it’s quietly siphoning millions from universities. The fix is both available and practical: add identity verification at the exact point where sensitive changes happen.
For faculty and students, it’s 30 seconds of extra security. For universities, it’s the difference between a secure paycheck and a stolen one.
Contact us to learn how to implement identity verification on your campus.