CXM & contact center identity
Passwordless access for CXM
Give every agent biometric access to shared workstations with one device per station that covers OS, VPN, and application login across every shift.

What’s broken today
Most MFA isn’t built for secure contact centers
No phones, no MFA apps
Secure floors block phones and email, so passcodes never reach agents and MFA breaks at OS and VPN login.
Tokens built for people, not stations
Per‑user security keys don’t match shared desktops and shifts, forcing more devices per floor and leaving tokens easy to lose, forget, or share.
High attrition, higher hardware churn
Agent turnover fuels constant token loss and recovery, stalling shifts and steadily driving up hardware costs.
Passwords keep fraud in play
Shared passwords and reusable tokens hide who logged in, complicating fraud investigations and customer audits.

What’s broken today
Most MFA isn’t built for secure contact centers
No phones, no MFA apps
Secure floors block phones and email, so passcodes never reach agents and MFA breaks at OS and VPN login.
Tokens built for people, not stations
Per‑user security keys don’t match shared desktops and shifts, forcing more devices per floor and leaving tokens easy to lose, forget, or share.
High attrition, higher hardware churn
Agent turnover fuels constant token loss and recovery, stalling shifts and steadily driving up hardware costs.
Passwords keep fraud in play
Shared passwords and reusable tokens hide who logged in, complicating fraud investigations and customer audits.

What’s broken today
Most MFA isn’t built for secure contact centers
No phones, no MFA apps
Secure floors block phones and email, so passcodes never reach agents and MFA breaks at OS and VPN login.
Tokens built for people, not stations
Per‑user security keys don’t match shared desktops and shifts, forcing more devices per floor and leaving tokens easy to lose, forget, or share.
High attrition, higher hardware churn
Agent turnover fuels constant token loss and recovery, stalling shifts and steadily driving up hardware costs.
Passwords keep fraud in play
Shared passwords and reusable tokens hide who logged in, complicating fraud investigations and customer audits.

450K
active users deployed globally
10M+
weekly authentications
6 months
from pilot to full global deployment
450K
active users deployed globally
10M+
weekly authentications
6 months
from pilot to full global deployment
450K
active users deployed globally
10M+
weekly authentications
6 months
from pilot to full global deployment
How we help
Biometrics built for shared workstations
1Kosmos delivers biometric authentication for secure shared desktops where per-user tokens and passwords don't fit the operational model. One device per station, every shift covered.
One key per station
Anchor one biometric device to each shared desktop, so every agent across every shift uses the same key with no personal tokens to issue or recover.
One key per station
Anchor one biometric device to each shared desktop, so every agent across every shift uses the same key with no personal tokens to issue or recover.
One key per station
Anchor one biometric device to each shared desktop, so every agent across every shift uses the same key with no personal tokens to issue or recover.
Passwordless from desktop to apps
Use a single fingerprint to move agents from Windows login through VPN or VDI and into customer applications, so every hop is tied to a verified identity.
Passwordless from desktop to apps
Use a single fingerprint to move agents from Windows login through VPN or VDI and into customer applications, so every hop is tied to a verified identity.
Passwordless from desktop to apps
Use a single fingerprint to move agents from Windows login through VPN or VDI and into customer applications, so every hop is tied to a verified identity.
Dramatically lower hardware costs
Cut hardware deployment by 75% or more by sharing one biometric device across multiple shifts instead of issuing personal tokens to every agent.
Dramatically lower hardware costs
Cut hardware deployment by 75% or more by sharing one biometric device across multiple shifts instead of issuing personal tokens to every agent.
Dramatically lower hardware costs
Cut hardware deployment by 75% or more by sharing one biometric device across multiple shifts instead of issuing personal tokens to every agent.
Track every sign‑in
Tie each login to a verified agent on a specific workstation so shared passwords, loaned hardware, and “it wasn’t me” excuses disappear from your fraud investigations.
Track every sign‑in
Tie each login to a verified agent on a specific workstation so shared passwords, loaned hardware, and “it wasn’t me” excuses disappear from your fraud investigations.
Track every sign‑in
Tie each login to a verified agent on a specific workstation so shared passwords, loaned hardware, and “it wasn’t me” excuses disappear from your fraud investigations.
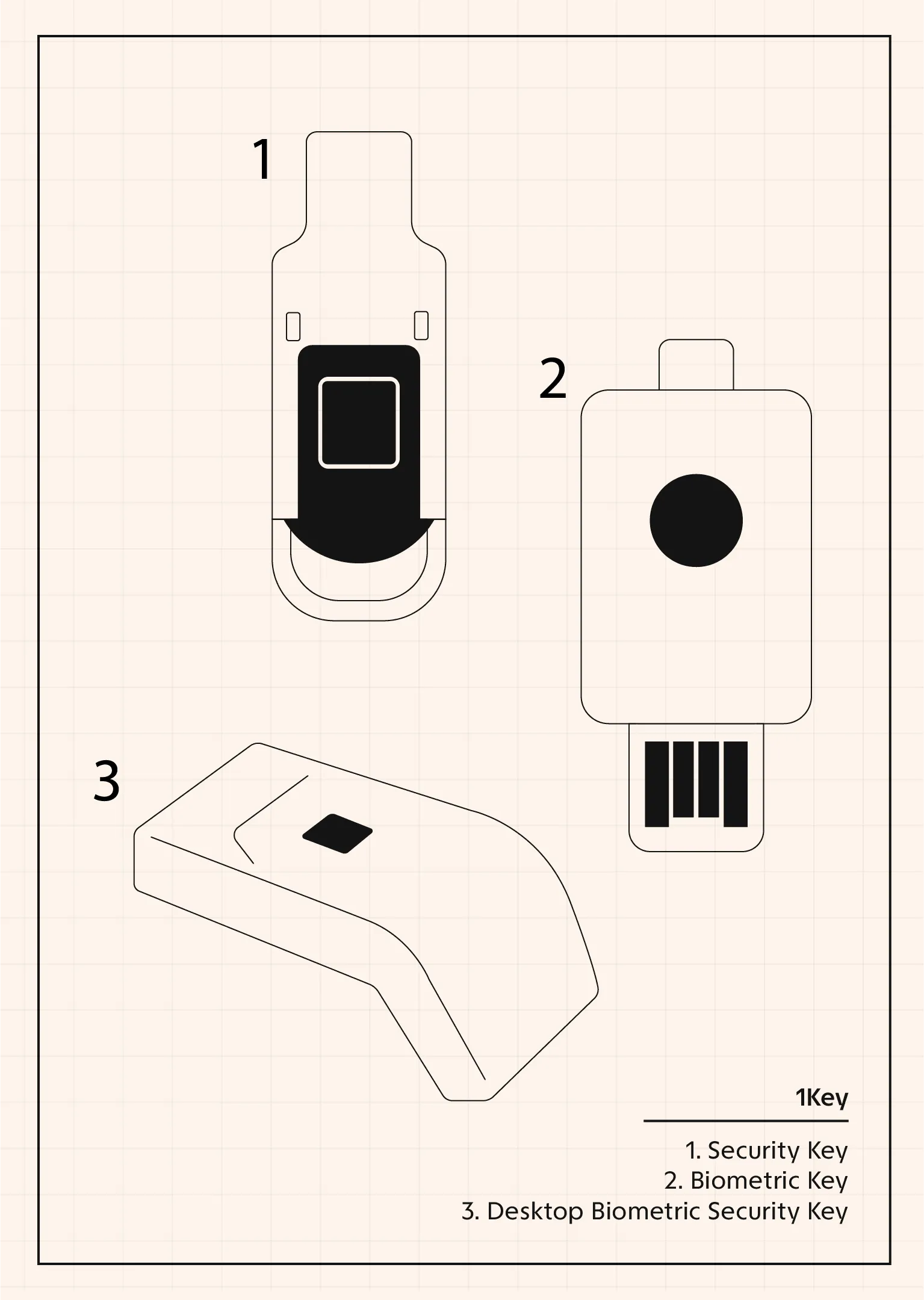
1Key by 1Kosmos
Shared workstation key
A biometric 1Key device (USB Type‑A or Type‑C) that stays with each shared desktop, letting every shift authenticate to Windows, VPN, and apps without personal tokens or passwords.
Shared workstation key
A biometric 1Key device (USB Type‑A or Type‑C) that stays with each shared desktop, letting every shift authenticate to Windows, VPN, and apps without personal tokens or passwords.
Shared workstation key
A biometric 1Key device (USB Type‑A or Type‑C) that stays with each shared desktop, letting every shift authenticate to Windows, VPN, and apps without personal tokens or passwords.
Per‑user biometric and touch keys
1Key also includes FIDO‑based biometric and touch security keys for individual users where personal devices, not shared workstations, are a better fit.
Per‑user biometric and touch keys
1Key also includes FIDO‑based biometric and touch security keys for individual users where personal devices, not shared workstations, are a better fit.
Per‑user biometric and touch keys
1Key also includes FIDO‑based biometric and touch security keys for individual users where personal devices, not shared workstations, are a better fit.


The 1Kosmos platform
Identity Verification (IDV)
Enroll every agent once with strong identity verification so that shared-workstation logins are tied to real-world identities.
Identity Verification (IDV)
Enroll every agent once with strong identity verification so that shared-workstation logins are tied to real-world identities.
Identity Verification (IDV)
Enroll every agent once with strong identity verification so that shared-workstation logins are tied to real-world identities.
Passwordless Authentication
Replace passwords with biometric sign in at shared workstations, then extend that security across desktops, VPN, and client apps.
Passwordless Authentication
Replace passwords with biometric sign in at shared workstations, then extend that security across desktops, VPN, and client apps.
Passwordless Authentication
Replace passwords with biometric sign in at shared workstations, then extend that security across desktops, VPN, and client apps.
Reverification
Automatically reverify agents when roles or risk change, and ensure their access always matches who they are.
Reverification
Automatically reverify agents when roles or risk change, and ensure their access always matches who they are.
Reverification
Automatically reverify agents when roles or risk change, and ensure their access always matches who they are.
Blog
Read our insights.
A collection of news, insights, and tutorials.
Enter our orbit.
The latest in identity security.
Blog
Read our insights.
A collection of news, insights, and tutorials.
Enter our orbit.
The latest in identity security.
Blog
Read our insights.
A collection of news, insights, and tutorials.
Enter our orbit.
The latest in identity security.

Transform how you verify and authenticate
Secure onboarding, eliminate passwords, and stop fraud on one platform. Schedule a demo and see it in action.

Transform how you verify and authenticate
Secure onboarding, eliminate passwords, and stop fraud on one platform. Schedule a demo and see it in action.

Transform how you verify and authenticate
Secure onboarding, eliminate passwords, and stop fraud on one platform. Schedule a demo and see it in action.





