The 1Kosmos Architectural Advantage
Why BlockID
High Accuracy
User Convenience
Flexible Use Cases
Key Benefits

FIDO2 Certified Biometrics
1Kosmos BlockID is FIDO certified which means the platform has undergone rigorous testing to verify quality coding and ensure the use of common devices to securely authenticate into web services. When combined with a verified identity, these deliver unmatched security and convenience.
FIDO supports hardware-based token authentication, including using USB keys, keycard authentication, finger print readers, and hardware tokens and provides a robust framework to implement passwordless authentication without having to lock into a single vendor or service provider.
With FIDO biometrics, you’ll also get the benefits of stronger security using physical traits (for example, including a fingerprint scan in a USB security key or leveraging FIDO-compliant facial recognition) in a Windows laptop.
Additionally, the FIDO Metadata Service provides an extensive directory of compliant technology so you can trust any component or solution you adopt.

iBeta Certified Biometrics
Biometrics can improve security by replacing passwords, but they can be subject to theft, spoofing and decisioning bias. iBeta is an independent NIST accredited biometrics testing lab that has developed certification programs to verify biometric applications perform to recognized standards.
In their Liveness certification, iBeta certified the 1Kosmos BlockID platform achieved a false match rate (FMR) of less than 0.1% at 95% confidence interval (in iBeta’s 21 CFR 1311.116 test).
When enrolling with BlockID, the user can perform an advanced form of biometrics called a liveness test. This biometric identifier eliminates any risk of facial spoofing, which is the task of creating false facial verification by using a photo, video, mask or a different substitute for an authorized person’s face. The liveness test is then leveraged for authentication.

Biometric Encryption
Biometric encryption uses a biometric template and public-private key pair to encrypt and decrypt personally identifiable information for authenticating a user into a digital service. This approach relies on the uniqueness of biometrics to ensure that hackers cannot reverse-engineer a password or key. Without the biometric and matching private key, all data in the digital wallet is not accessible, usable or even legible.
Biometric encryption minimizes attack surfaces involved in authentication, namely through strong storage of biometric information and the elimination of passwords. In BlockID there is no central storage of user biometrics, this makes it easier to ensure all user biometrics remain private.
Biometric authentication adds a layer of protection by foregoing the need to store or transmit a password or biometric template. Biometrics also require minimal user training. They are easy to use and can be rapidly adopted across the organization.
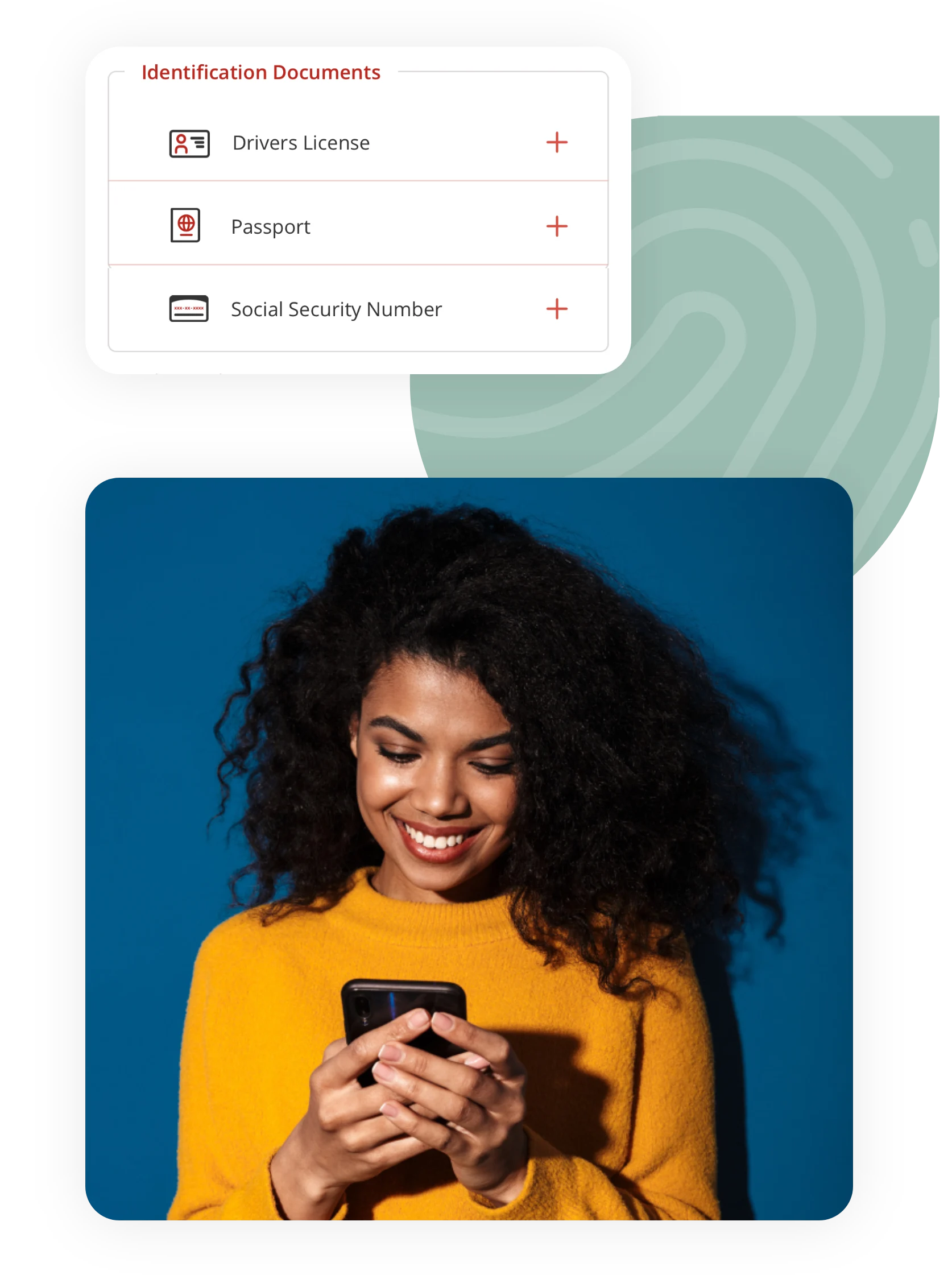
Flexible Levels of Identity Assurance
With 1Kosmos BlockID you determine the type of biometric appropriate for a given application and the level of identity assurance appropriate for the business risk. For Know Your Customer (KYC) and Know Your Business (KYB) standards, Identity Assurance Level 2 can be achieved by using LiveID in combination with identity verification using government issued credentials, such as a driver’s license, id card or passport. (The platform also supports a path to IAL3 via video or in-person supervised sessions.) LiveID ensures liveness and verifies in real-time a user’s facial match to the enrolled biometric and verified documents.
Lesser forms of identity assurance are available using information from banking, telco or corporate databases. Depending on the business need 1Kosmos BlockID can also support “inferred” identity, where a user’s access to an email address or logged in device can provide verification adequate for the intended use. The biometrics used in all cases can include device-level face and fingerprints, USB devices with fingerprint readers, iris/retinal scans, voice recognition systems, etc.
For additional use cases, 1Kosmos can also verify a user’s social security number (SSN) against the SSA, verify a driver's license to the American Association of Vehicle Administrators (AAMVA) or verify if a user is indeed a physician by validating their NPIN (National Physician Information Number). As the documents and accounts are enrolled, the location and phone number are verified against the issuing authority. Then, the user's LiveID scan is validated against the picture extracted from the document. Once the identity is validated, their biometrics are enrolled, and the data is encrypted with the user’s private key and stored in the 1Kosmos private and permissioned blockchain.