Easy Integration for Web-Apps Using OAuth2/OIDC
New configuration wizard for SSO through OAuth2/OIDC
1Kosmos always supported deep OpenID Connect core capabilities by implementing the openid-connect-core specification. With the latest release, we are thrilled to announce support for modern federation and authorization standards with OAuth 2.0 (RFC 6749). We will also take the opportunity to showcase application integrations with our OIDC App Integrations feature in AdminX.
With this release we allow for advanced PKCE enabled authorization-code based OAuth2 flows for integrating OIDC applications that provide administrators an interface for providing seamless SSO experiences to end users.
What is OpenID Connect?
OpenID Connect is an open identity standard. It acts as an authentication layer (proving who you are) on top of the OAuth 2.0 authorization standard (granting you access).
An OpenID Connect (OIDC) app integration provides identity federation after a user has been deemed authorized via one of the various OAuth 2.0 protocol flows supported by 1Kosmos. OIDC is used by a relying (receiving) party to verify end-user identity and obtain specific user information subject to consent granted by that same end-user.
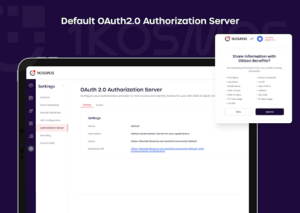
Your Community Authorization Server
Every community comes with a built-in authorization server called the Default Authorization Server. The base URL for the Org Authorization Server is https://<tenantname>/community/default. You can access your Community Authorization server from the AdminX portal. Documentation available here.
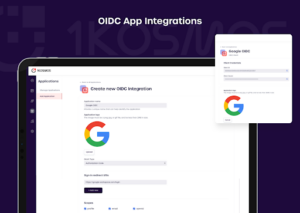
Create OIDC App integrations using a wizard
The control plane allows administrators to create a new client that can leverage OIDC to create SSO flows for web apps. Start by creating a new client and choose the scopes that need to be verified for the user. Your client ID & credentials are automatically generated and will be required to perform configurations on the relying party.
User Consent for OAuth 2.0 and OpenID Connect Flows
A consent grant is a user’s explicit permission to allow an application to access resources protected by scopes. As part of an OAuth 2.0 or OpenID Connect authentication flow, you can prompt the user to approve your integration’s access to specified resources, or set up user consent as part of creating the integration.
If user consent is required for certain scopes, the administrator can choose to present consent screens to the user.