Continuous Authentication: A Dynamic Approach to User Verification
Introduction
Cybersecurity is no longer just about setting a strong password or having an encrypted connection. As digital threats have evolved, so too have the mechanisms to counteract them. Continuous authentication offers a fresh perspective, moving beyond the initial login verification to ensure secure identity verification a user remains genuine throughout their session.
How can organizations maintain top-notch security as threats become more intricate without hampering user experience? That’s exactly what we are going to cover in this blog post.
Key Takeaways
- Evolving Security Paradigm: The evolution of cybersecurity from simple password-based protection to continuous authentication reflects the need for a dynamic approach that monitors user behavior throughout their session to counteract evolving threats.
- Integration and Fortification: Continuous authentication’s strength lies in integration with other security systems, such as intrusion detection, firewalls, and SIEM, forming a multi-layered defense strategy against cyber threats and minimizing potential breaches.
- Balancing Costs and Benefits: While initial costs are associated with implementing continuous authentication, the potential savings from preventing breaches, reducing downtimes, and enhancing user trust make it a strategic choice with a clear Return on Investment (ROI).
The Evolution of Authentication Methods
The evolution of authentication methods has responded to the ever-growing sophistication of cyber threats. Here’s a look at how these methods have developed over time:
- Password-based authentication: Once upon a time, a strong password was deemed the gatekeeper of digital information. But as hacking tools improved, merely having a complex password combination wasn’t enough. Intruders found ways to decipher logic credentials, leading to unauthorized breaches and compromised passwords.
- Two-factor & Multi-factor authentication: Recognizing the limitations of single-password protection, the digital security community introduced multi-layered authentication verifications. This involved not only something users know (password) but also something they have (a mobile device, for instance) or something they are (biometrics).
- Biometrics: Biometrics brought forth unique identifiers such as fingerprints, retina scans, and facial recognition. These, being unique to individuals, offered a more personalized security approach. But, even then, once authenticated, the user had unlimited access until logout.
Our journey in the authentication realm began with simple password systems called single-factor authentication. As threats evolved, so did the checks, leading to two-factor authentication, knowledge-based authentication (like secret questions), and possession-based authentication (like smart cards or tokens).
While all these methods offer levels of protection, they’re typically static, emphasizing the need for the dynamic verification processes we see today.
Integration with Other Security Systems
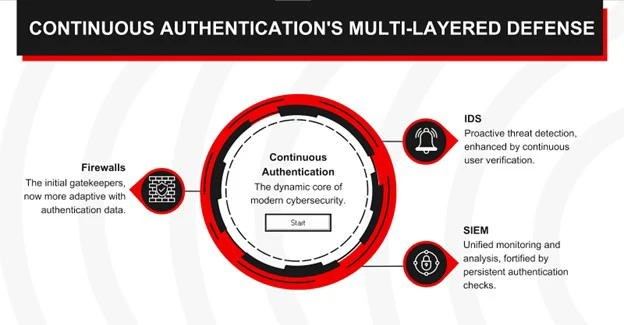
Continuous authentication, while powerful on its own, achieves its full potential when integrated with other security systems. Here’s how such integration can fortify your defense against cyber threats:
- Integration with Intrusion Detection Systems (IDS): IDS ensures that any abnormal behavior can be flagged in real-time, even if authenticated. This proactive approach drastically reduces the window of opportunity for malicious actors.
- Empowering Firewalls: Firewalls are the first line of defense against cyber threats. They can be more adaptive when fed with continuous authentication functionality and data, allowing them to respond quickly to potential threats.
- Unified Dashboard with SIEM Systems: Integrating continuous authentication with Security Information and Event Management (SIEM) systems creates a unified dashboard where multiple security events can be monitored and analyzed concurrently, ensuring no threat slips through the gaps.
By fusing user authentication with these vital security components, organizations can establish a multi-layered defense strategy that efficiently safeguards their digital landscape against evolving cyber risks.
Cost Implications and ROI
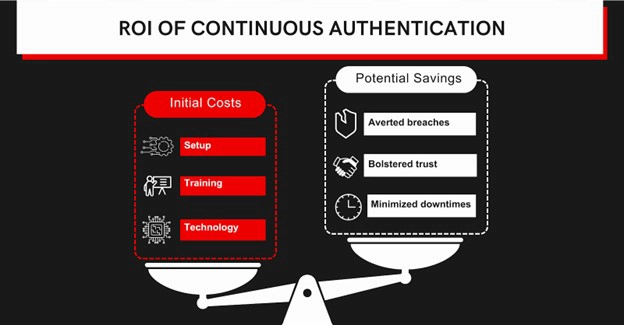
The financial implications of implementing continuous authentication are twofold:
- First, there’s the direct cost associated with setting up the system, which includes the technology, infrastructure, and manpower.
- Second, there are indirect savings – reduced potential losses from breaches, decreased downtimes, and enhanced user trust.
The ROI for continuous authentication becomes evident when weighed against the financial and reputational damage caused by data breaches – which can run into millions or even billions of dollars. For decision-makers, understanding this balance is crucial.
The initial investment in a continuous authentication solution can prevent far more significant potential losses, making it a strategic choice rather than just a cost.
User Education and Training
While technology forms the backbone of continuous authentication, users significantly influence its efficacy. Organizations should prioritize user education and training. By making users aware of the reasons behind constant checks and their benefits, resistance to adoption can be reduced.
Training sessions can familiarize users with the new processes, helping them understand the nuances and the importance of their role in this system. Cultivating a security-first mindset ensures that the authentication system functions seamlessly and that individual users are partners in the organization’s security endeavors, not just passive participants.
Future Innovations in Continuous Authentication
The realm of continuous authentication is ripe for innovations. With advancements in AI, the capacity for real-time behavioral analysis is set to grow exponentially.
Biometrics, too, is seeing a surge in research, with possibilities ranging from gait analysis to biometric authentication to heartbeat recognition.
The most exciting frontier is quantum computing. With its ability to process vast amounts of data at unprecedented speeds, quantum computers can revolutionize how the authentication process analyzes and responds to potential cybersecurity threats.
Such advancements ensure that continuous authentication remains adaptive, evolving with the ever-shifting cybersecurity landscape.
Comparison with Traditional Methods
Continuous authentication methods and traditional methods clearly distinguish their efficacy. Traditional methods, like single-factor authentication, rely on one-time checks, making them susceptible to breaches post-verification.
In contrast, continuous authentication remains vigilant throughout a user session, offering dynamic protection. While traditional methods might be less resource-intensive upfront, they can be costly in the long run, given their vulnerability to breaches.
Continuous risk-based authentication, with its initial investment, offers a more fortified defense. For organizations making a choice, the question becomes: “Is it more prudent to invest now and be secure or save now and risk potential breaches?”
Now that we got familiar with the evolution of authentication methods let’s explore deeper what Continuous Authentication exactly is.
Understanding Continuous Authentication
Unlike earlier methods, continuous risk-based authentication isn’t a one-time identity verification. It actively and unobtrusively monitors users, ensuring they’re who they claim to be every second of their session. This approach enhances security and aligns with the modern demand for seamless user experiences.
The fundamental cornerstone of this method is risk-based authentication. Instead of merely accepting a user post-login, the system consistently evaluates the risk associated with the user’s behavior and actions. Depending on the perceived threat, it either allows access or triggers additional security measures.
Specific Threats Continuous Authentication Mitigates
Continuous authentication addresses several modern-day cyber threats that more traditional authentication methods might overlook.
One looming threat is session hijacking, where a malefactor takes over a user’s session post-authentication. This method bypasses initial login checks, making continuous verification crucial.
Then there’s the risk posed by insiders – employees with malicious intent or compromised accounts. User authentication helps detect unusual behavioral patterns, ensuring that an insider doesn’t misuse their privileges.
Lastly, while credentials might be compromised, mimicking user behavior throughout a session is a tall order, making continuous checks a robust deterrent against such breaches.
Now that we have a brief understanding of what continuous authentication is, let’s delve into key components of how it works.
How Continuous Authentication Works
Continuous account Authentication offers a sophisticated and dynamic approach to verifying identities. This multi-faceted process leverages various techniques and factors to ensure ongoing user validation:
- Behavioral Biometrics: Everyone has unique ways they interact with their devices. Some might type rapidly, others more deliberately. These interactions, like keystroke dynamics or mouse movement patterns, are invaluable for continuous verification behavioral biometric authentication. These patterns remain consistent over time and are challenging to replicate.
- Contextual Attributes: The context surrounding user activity offers numerous clues. Is the user logging in from a previously unrecognized device? Is the IP address from a different country than usual? Such deviations can indicate a potential breach of user identity verification and are considered in real-time by continuous authentication systems.
- Time-based Patterns: Humans are creatures of habit. If an employee routinely accesses the system during office hours, a sudden login at an odd hour could be considered suspicious behavior. Continual monitoring allows for instant risk assessment based on these patterns.
- Machine Learning & AI: The beauty of continuous authentication lies in its learning capabilities. Using AI, the system adapts to evolving and continuous user authentication behaviors, ensuring that genuine activities are rarely flagged and anomalies are swiftly identified.
Continuous Authentication with Typing Biometrics
Typing biometrics offers a unique dimension to continuous authentication. It isn’t merely about the password entered but how it’s typed: the rhythm, speed, and finger pressure used by keystrokes – can be as unique as a fingerprint.
The technology captures these nuances, creating a behavioral profile for users. Over time, systems recognize this pattern, ensuring that replicating the typing pattern becomes a formidable challenge even if someone knows your password. When integrated into continuous user authentication frameworks, such biometric data provides a dynamic layer of security that’s subtle and powerful.
Moving forward, it’s time to look deeper into the advantages of continuous authentication and what makes it a very important security solution.
Advantages of Continuous Authentication
Here are some of the most common advantages of continuous user authentication:
- Enhanced Security: Continuous authentication is akin to having a security guard who doesn’t just check IDs at the entrance and ensures only authorized personnel act within the premises. Continuously verifying users minimizes the window of opportunity for malicious activities.
- User Experience: One of the main drawbacks of heightened security has often been compromised user experience. Continuous user authentication sidesteps this by working seamlessly in the background, ensuring constant security checks do not inconvenience genuine users.
- Adaptable Security: Different users might present different risk levels. Continuous authentication scales its scrutiny based on perceived risk, ensuring that high-risk actions get attention.
- Reduction in False Alarms: Traditional systems might flag genuine actions as threats, leading to unnecessary disruptions. By understanding the user better, continuous authentication reduces such false positives.
Embracing these benefits of continuous authentication fortifies an organization’s defenses and paves the way for a more intuitive user experience. Yet, as with any evolving technology, specific challenges warrant consideration.
Challenges and Concerns
While the merits of continuous authentication are undeniable, it’s essential to approach this method with a holistic perspective. No matter how advanced, every technology comes with its challenges. Recognizing these concerns ensures that organizations are better prepared to address them:
- Privacy Concerns: Continuous monitoring, though for a noble cause, can raise eyebrows. Users might feel their privacy is invaded, leading to resistance against its implementation.
- Technical Hurdles: Implementing continuous authentication is more than just a plug-and-play affair. It demands a synergy of advanced tech infrastructure and skilled personnel to integrate it seamlessly.
- False Flags: No system is foolproof. There might be instances where genuine user actions are misconstrued as anomalies, leading to unwarranted security measures.
While these concerns present valid roadblocks, understanding them is the first step in addressing and mitigating potential issues. The ongoing evolution of continuous authentication hints at a transformative horizon.
Compliance with Security Standards
Adopting continuous authentication isn’t just about fortifying defenses; it’s also about aligning with global security standards. For instance, under GDPR, organizations must ensure data protection by design and default.
Continuous authentication aids in fulfilling this mandate. Similarly, adhering to HIPAA standards becomes paramount for industries dealing with healthcare data. Implementing ongoing checks can significantly reduce unauthorized data breaches, ensuring compliance. Non-adherence to such measures can lead to hefty penalties and reputational damage, making the case for continuous authentication even stronger.
All tech solutions need user acceptance and buy-in, irrespective of their brilliance. For continuous authentication work on an organization-wide rollout, users need to understand and appreciate the value continuous authentication brings.
So, keeping those challenges and concerns in mind, what is the future of continuous authentication and different continuous authentication methods? Let’s look into that next.
Future of Continuous Authentication
Continuous authentication stands out as a beacon, signaling the direction in which secure user verification might head. What does the horizon hold for this emerging authentication method? Let’s speculate on the coming developments:
- Predictive Analytics: The next frontier is not just to identify but also to predict. Systems can anticipate and ward off threats by understanding user behavior patterns and behaviors before they materialize.
- IoT Integration: With the proliferation of intelligent devices, the boundaries of what needs protection have expanded. Continuous authentication solutions can be pivotal in ensuring these devices remain uncompromised in a hyper-connected environment.
- Broader Applications: E-commerce platforms can leverage this tech to ensure transactional security, enhancing trust and minimizing fraud.
The horizon for continuous authentication seems promising, teeming with innovations and enhancements. As we advance, it becomes imperative for organizations not just to understand its potential but also to take proactive steps toward its implementation.
Implementing Continuous Authentication in Your Organization
The journey from traditional password-based systems to continuous authentication can appear daunting for many organizations. However, the transition can be smooth and rewarding with a structured approach and clear roadmap. If you’re contemplating the incorporation of continuous authentication within your organization, here are a few actionable steps:
- Evaluating the Need: The first step is introspection. Does your organization handle sensitive data? Are you a high-risk target for cyberattacks? If yes, this might be the upgrade you need.
- Implementation Roadmap: Identifying the need is just the start. Partnering with the right tech providers, setting up the infrastructure, and training stakeholders form the crux of the implementation journey.
- Monitor and Iterate: As with all tech solutions, continuous authentication is not a set-it-and-forget-it tool. Regular, continuous risk assessments ensure that it evolves with changing threats.
Venturing into continuous authentication is a strategic decision that demands thoughtful execution. With the right approach, organizations can enhance security and enrich the overall user experience in your organization.
Conclusion
In our exploration, it’s clear that continuous authentication marks a transformative shift in cybersecurity. Striking a balance between security and user-friendliness is essential. BlockID’s identity-based, passwordless approach embodies this transition. To understand how these developments translate into practical applications and to enhance your security strategy, explore BlockID with us. Schedule a call with our team to learn more.
