What Is Privileged Access Management?


Privileged Access Management, or PAM for short, is a crucial component of solid cyber defenses. It’s essential to restrict access to the most vital and sensitive parts of an organization’s information technology to the proper people.
Privileged access gives a user or program extensive permissions or visibility into a computer system. System administrators, database administrators, network engineers, and others who need comprehensive control over an organization’s IT infrastructure often demand privileged access.
There is a higher possibility of abuse or exploitation because of this accessibility. Privileged access is obviously a vital part of the whole cybersecurity ecosystem. The organization’s ability to withstand cyberattacks largely depends on how well this access is managed.
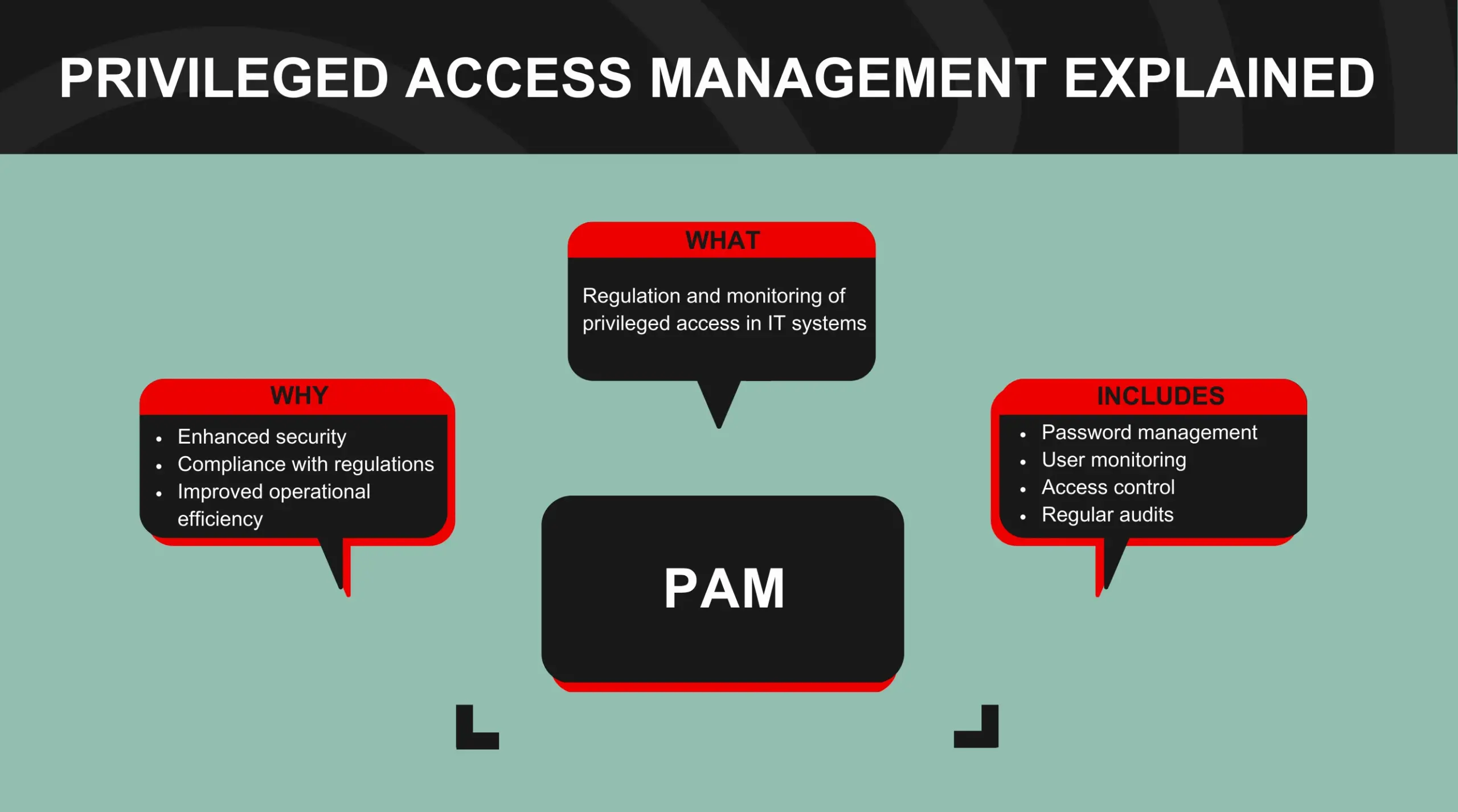
Privileged access management, or PAM, is a method enterprises use to monitor and control user access to sensitive data and systems. The primary objective is to ensure that access is granted only to those who need it and at the appropriate times. Privileged access management (PAM) is essential to any robust cybersecurity architecture since it reduces the likelihood of data breaches and other types of illegal access.
The primary means by which PAM accomplishes its aims is through centralizing the management of privileged access in its different forms. Password management, user activity tracking, and stringent enforcement of access limits are just a few examples.
PAM has several benefits that help an organization’s security measures immensely. To begin, PAM improves a company’s cybersecurity by increasing the effectiveness of existing security procedures and decreasing the likelihood of data breaches. It does this through meticulous access management, regular audits, and stringent control systems.
Compliance with several regulations is another area where PAM might be helpful. Access to confidential information must be protected in several industries due to legal requirements. By reducing the likelihood of incurring fines for failing to comply, an effective PAM strategy helps businesses achieve these demanding requirements.
Productivity enhancement is one of the many benefits of PAM. By streamlining processes and reducing the likelihood of internal threats, firms may benefit from a thorough awareness of “who has access to what.”
Creating an effective PAM strategy requires careful consideration of several factors. Locating and categorizing all privileged accounts is the first order of business. Given the impossibility of controlling unknown entities, compiling a list of all privileged accounts is a necessary first step.
The next stage is to put into practice the principle of least privilege (POLP), which guarantees that users have just the permissions they need to do their duties. The potential for abuse or exploitation may be minimized by restricting access.
The third essential feature is constant monitoring and auditing. If tracked carefully, suspicious behavior may be identified and dealt with before it leads to significant incidents.
Establishing safe procedures for requesting privileged access is the fourth stage. The organization’s security may be improved by requiring that access be allowed only after thorough verification has taken place.
Finally, it’s essential to monitor and change your passwords often. Changing passwords regularly helps prevent unwanted access that might result from leaked credentials.
Organizations should evaluate the characteristics of potential PAM solutions against their requirements. The best option will have thorough auditing and reporting capabilities, work seamlessly with current systems, and be expandable to meet the needs of a growing business. It is also important that it allows for strict policy enforcement.
There are several market-leading PAM solution vendors, each with its advantages. Therefore, businesses must carefully consider their unique requirements and goals and choose from many viable choices.
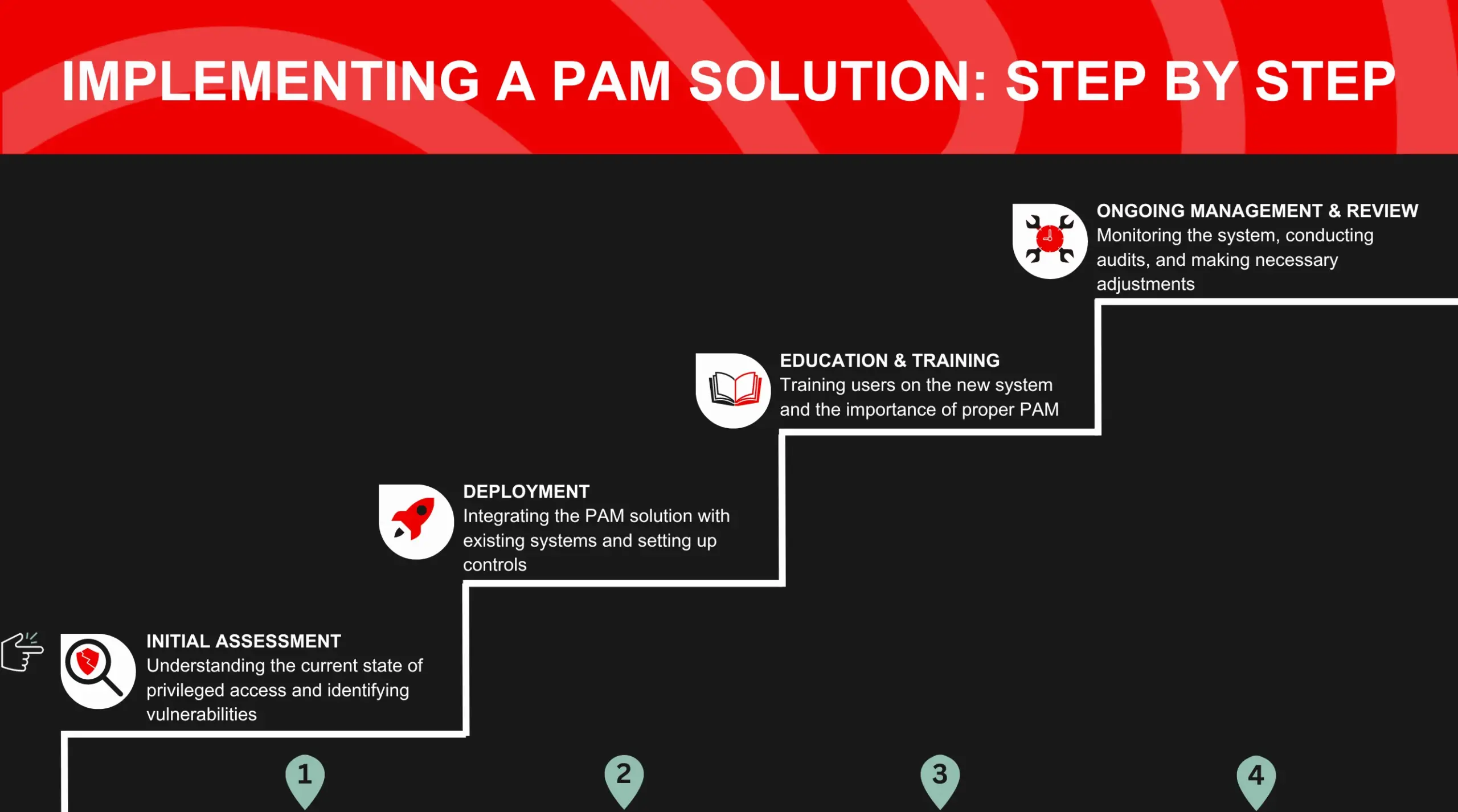
The first step in introducing a PAM solution is to evaluate the organization’s present privileged access situation. The PAM strategy may then be built around the findings of this evaluation, which pinpoints any weak spots. The next step is deployment, which entails connecting the PAM solution to the rest of the infrastructure and establishing the required safeguards.
The next step is educating users on the new system and the significance of good privileged access management. Training employees on the new system and their part in ensuring security is essential.
Management and evaluation are ongoing, which completes the process. The effectiveness of the PAM approach in the face of the ever-evolving cybersecurity scenario is ensured by regular monitoring, audits, and modifications.
Strong cybersecurity must always include Privileged Access Management. Any business serious about protecting its digital assets should invest in it because it can improve safety, compliance, and productivity.