Decentralizing Identity for Enhanced User Control
As human beings, we have an innate desire to own what we create. Our identity is no different. In the physical world, a person who wants to prove their identity usually does so via a driver’s license or a physical identity card. After presentation, the physical identity card goes right back into the user’s physical wallet, which means they get to retain control over their identity.
Compare and contrast this with a user who makes online payments on eCommerce websites, or makes travel bookings using credit cards and PayPal. The user does not keep their digital identity in their “digital wallet”, because normally no such thing exists. Usually, users have no control over where the data they present for identification is stored, or what happens to it after the transaction is over. The same is true for social media accounts as well, despite the walled gardens the social media companies create around our digital identity, it is within that boundary that most data infractions occur.
Businesses also collect and store their employees and contractors data for the purpose of doing business. Data exchange between businesses usually takes place via third-party providers who store the data in their private vaults. This calls for a trustworthy and reliable system that enables users, business to interact digitally with other users and businesses but do so in a secure and privacy preserving manner.
Legacy of Central Identity Management
As digital identity is used inevitably in various walks of life, a centralized approach to identity management has become increasingly problematic. Central or legacy identity management seems like a good idea, but it lends itself to more problems than solutions, unfortunately. For one, the user is not in control of their own identity, and while this might be in line with workforce use cases, for consumer use cases it is a privacy destroying mechanism.
Another issue with centralized identity is that it leads to identity data that is not in “sync” with the user’s latest activity. This does not bode well for continuous authentication and continuous transaction authorization use cases that require real time context for decision making.
Centralized identity management is also not quite aligned with the way people transact and behave across various physical and digital worlds either. It introduces mandatory processes that verify, validate and manage the identity through its life cycle. Over time, these processes nearly always become prohibitively costly, repetitive and cumbersome, necessitating manual data reconciliation and validation processes in the background.
Decentralization, Blockchain Technology and the Self Sovereign Identity
Decentralization of Identity is defined as the ability of an ecosystem to shift control of user identity from a central authority over to a distributed network where the ultimate authority remains with the user.
In simple words, end users must be able to control their personal information on local devices they own. This could include but not be limited to browsing history, medical information, financial records, etc. retaining the ability to share the data with third-party entities, while maintaining the authenticity and trust using cryptographic signatures.
With decentralized systems and sensibly choreographed cryptographic ceremonies, the users fully control their private information, without losing data authenticity and integrity as it is securely shared on a network.
Self-sovereignty is the right of users to own and control their own identity online and be the final arbiter of who can access and use their data and personal information. Self-sovereign identities are a concept for establishing digital identities that allows for such management of identity using numerous, comparatively complex layers of cryptographic ceremonies to offer full data ownership back to the user.
The idea behind the technology is to allow users to self-manage their identities without having to depend on third-party providers to central store and manage data.
Self-sovereign identity transfers control over to a user.
Decentralized Identity Concepts
In light of the discussion above, the essential challenge is how to establish and retain trust without possessing any direct evidence or references for the claims made by the user, device or machine. Ultimately, we need a way to identify a single identity and recognize it nationally, internationally even, while solving cross-platform interoperability challenges.
NIST comes to our aid somewhat, with an introduction of a concept called the Trust Anchor:
“A public or symmetric key that is trusted because it is directly built into hardware or software, or securely provisioned via out-of-band means, rather than because it is vouched for by another trusted entity (e.g. in a public key certificate).”
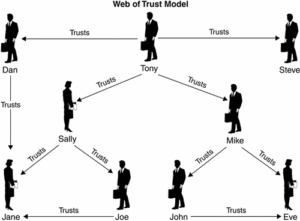
The web of trust relies on current PKI mechanisms to confirm the identity. In the scenario where the updated certificate must be provisioned, we can be moderately sure that the new certificate is transmitted to the device eligible to receive it.
According to Gartner:
“By 2024, a true global, portable, decentralized identity standard will emerge in the market to address business, personal, social and societal, and identity-invisible use cases.”
Distributed Ledger Technology
Distributed Ledger Technology (DLT) refers to the protocols that allow simultaneous access, validation, and record updating in an immutable manner across a network that’s spread across multiple entities or locations. Commonly known as Blockchain, DLT offers an opportunity to change the way individuals and organizations manage their private data. It enables more accountability and enforces a higher level of privacy by design. The data flow is regulated via distributed ledger and not controlled by anyone centrally.
Decentralization technology such as distributed ledger as well as Blockchain can be used to create identity management services.
Blockchain, for example, is a growing list of records, called blocks that are linked together using cryptography. Blockchains are resistant to modification of their data because once recorded, the data in any given block cannot be altered retroactively without altering all subsequent blocks. The Identity wallet provides the ability to generate, bind, secure and maintain attributes or information of a user’s identity.
Blockchains have three traits that make the basis of trust. Firstly, anyone can be a participant by contributing their computing resources – since a prior linkage to any other node in the system is not necessary. Secondly, adding a new block on the blockchain is radically expensive computationally, as the consensus mechanism is developed to necessitate a specific amount of wall-clock time to complete irrespective of the network’s size. And lastly, it is not possible to forecast which contributor will be the first to add the next block. The key advantage of the blockchain is trust between the stakeholders, and to form a history of transactions that is incredibly hard to alter.
While we are talking about the benefits of using blockchain for identity management, we should also mention differences between public and private blockchains.
Public Permissionless Blockchain
A public blockchain is the permission-less distributed ledger technology where anyone can join and do transactions. Each peer has a copy of the ledger, which also means that anyone can access the public blockchain if they have an internet connection. Bitcoin is an example of a public blockchain.
The verification of the transactions is done through consensus methods such as Proof-of-Work(PoW), Proof-of-Stake(PoS), and so on. At the cores, the participating nodes are required to do the heavy-lifting, including validating transactions to make the public blockchain work.
These lack transaction speed, with transactions taking from a few minutes to a few hours. This is because it takes time to solve the mathematical problems and then complete the transaction. They are also not scalable because growth of the blockchain introduces even more work on the existing nodes.
Private Permissioned Blockchain
A Private blockchain is deployed in a controlled network and under the control of a governing entity. They still provide the necessary security and durability functions, of transparency, trust, and security to the selected participants.
Deploying a private and permissioned blockchain in the enterprise serves to move away from the cryptocurrency focus in blockchain adoption and it helps immensely that a private and permissioned blockchain improves upon a public and permissionless one.
According to Gartner:
“By 2023, 35% of enterprise permissioned blockchain applications will integrate with decentralized applications and services.”
Public blockchains let anyone join the system but in a private blockchain, users have to be “on boarded” or, in other words, granted permission. From an administrative perspective, the authority to write a user’s data into the blockchain is the sole responsibility and authority of the blockchain’s identity custodian – the Enterprise.
A blockchain deployment that is private and permissioned, can be primed for digital identity transformation using a distributed identity model. Private Blockchains are designed for enterprises that want to have more control over data and want more privacy with fine grained permission control.
Verifiable Claims
We will wrap up this introductory blog with a mention of verifiable claims. Verifiable claims are a mechanism for users to share assertions about themselves without having to disclose their identity. These assertions may be representation of a user’s claim to a service, or a transaction worthy of record.
A decentralized identity management system is of not much value without the issuers of verifiable claims. Enterprises and educational institutions alike, can issue credentials to users represented by verifiable claims (diplomas, degrees, work authorization, etc) and via an established protocol, allow for those verifiable claims to be presented when challenged for proof that they do indeed have that diploma, or that work authorization.
This blog series on decentralized identity will explore these topics in more detail.
