Identity Solutions: What To Look For
An identity solution can be the difference between keeping your data secure and allowing hackers access to any digital information in your business.
So what is an identity solution? An identity solution helps manage digital identities while also ensuring users are who they say they are when they log in. It can also help with controlling digital access to specific data or documents across the company.
Some of the top IAM and IDaaS providers include:
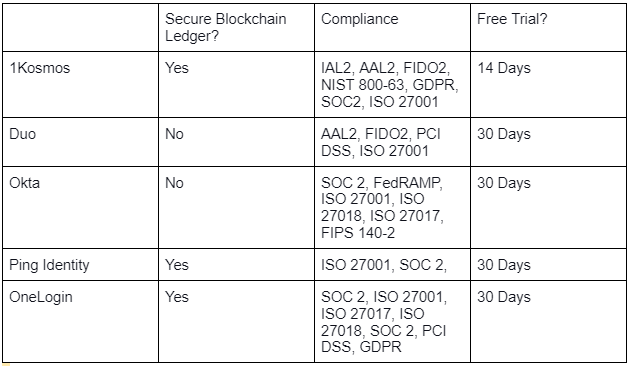
- 1Kosmos
- Okta
- Duo
- Ping Identity
- ForgeRock
- OneLogin
What Is Identity and Access Management, and Why Do I Need an Identity Solution?
Identity and Access Management (IAM) is a framework for managing permissions, access policies, and authentication within a digital system. As the name suggests, IAM is comprised of two broad and overarching categories:
- Identity Management: identity management is creating, maintaining, and securing digital identities within a given system. A digital identity can be any combination of information used to identify users for system access and administration and can include data like usernames and passwords, biometric templates, or even Personal Identifiable Information (PII).
- Access Management: Once a user accesses or moves through a digital system, access management determines the policies and permissions that apply to that user for rights to system information or resources. An access management system will protect resources from unauthorized access once a user is identified correctly.
The central concept of an IAM system is that both authentication and authorization for resources are closely related and should be managed as such. However, it is not the case that they are interchangeable with one another.
An identity solution emphasizes the user identity and authentication aspect of system security. Identity Management systems (also known as IdM systems) will typically handle the following functions:
- Identity Creation: An integral part of IAM is giving admins or more commonly users the ability to onboard their identities into the system. At this stage, the user can provide information as dictated by the system. This information will be used to verify the user’s identity during any instance they seek to access. The most common form of identity onboarding you’ll see in consumer apps is an email or username and a password. You’ll see more involved onboarding for enterprise systems and many cloud apps that include biometric information (like fingerprint scans or facial scans) or second-factor authentication information (like a phone number for SMS verification or email for a secure link verification system).
- Authentication: At the point of user access, the IdM will verify the user by comparing provided credentials with credentials stored in the IdM. If there is a match, the user is authenticated and granted access to information and resources as permitted by their role or other permissions.
- User Management: An IdM will also include some method of storing user identities. In older models (some of which are still currently used), an IdM might be as simple as a database of user IDs and passwords. More modern systems employ storage tools to manage continuity and resiliency while including advanced security and privacy controls.
What Is the Difference Between an Identity Solution and Password Management?
It’s important to note that any contemporary IAM or IdM is much more than a storage repository for user information. In the older days of internet communication and limited server resources, many businesses relied on secure databases to handle basic ID management. While this approach isn’t sustainable for a serious business organization, this model can work for end users.
In the past few years, there has been a growth in password management tools for end users. In the most basic sense, a password management solution helps users securely store username and password combinations across various accounts. The benefits of this are primarily the following:
- Secure management of passwords: As the name suggests, users can securely store passwords in a central repository. This means no sticky notes and no plain text files on local machines to manage their login credentials.
- Streamlining of password usage: Most password managers will include plugins for popular browsers like Chrome or Firefox that can recognize login pages and provide the correct credentials for the user. This makes it that much easier to navigate through different accounts.
- Encouraging strong passwords: Considering the first two benefits, the user, now unburdened from remembering or fetching passwords, can use more complex passwords with more extensive character variety and non-standard words to improve security.
An identity management service is more involved than just managing passwords. For example, an IdM emphasizes managing identities as a whole, storing and coordinating user identities across an entire spectrum of data.
Because IAM employs authentication and identity management, you are essentially looking at different products. However, it would help your organization deploy both of these solutions as a complete and secure package if you plan to include passwords as part of your IAM.
What Should I Look for in an Identity Solution?
Even if you have incredibly unique systems and services, your IdM solution should include a series of standard features. These features include the following:
- Security: Any authentication scheme should adhere to clear privacy controls and the prevention of unauthorized access. This includes strong authentication controls, identity checking, and secure credential storage.
- Privacy: Many user accounts will include some form of PII. In these cases, you must protect the privacy of that data beyond simply securing it from theft. Confidential controls for internal use and processing, as well as maintaining data integrity, are important aspects of privacy.
- Compliance: Your solution should help you meet or exceed compliance requirements in your industry. Whether it’s HIPAA, PCI DSS, GDPR, SOC 2, or any government or business-specific framework, your solution should provide the security and the privacy controls to meet those obligations.
- Multi-Factor Authentication: Modern authentication at the level of enterprise use should always contain some form of MFA. This includes any form of MFA but in particular strong MFA like biometrics.
- Integration with Existing Systems: A strong identity solution will integrate easily with existing infrastructure or, if possible, provide a seamless way to work with identities and authentication between one system and the next (for example, with a cloud Authentication-as-a-Service product).
- Flexibility and Scalability: A modern IdM will include some form of support for mobile devices, laptops, and remote authentication, including leveraging modern mobile tools like cameras and facial scanners.
- Passwordless Experience: While passwords are common, passwordless solutions that use biometrics and identity proofing to remove the need for password memorization are strong forms of authentication that cut out the weakest aspect of security: the end user.
- Cloud-Based: Many authentication providers are switching to ID-as-a-Service (IDaaS) to support cloud platforms. These services are often better positioned to support cloud applications and distributed workforces than on-premise solutions.
Top IAM Providers in 2021
The Next Step in Authentication Evolution with 1Kosmos BlockID
All these features are ideal, but they aren’t worth much if the system isn’t preparing for the future of identification. 1Kosmos has created a system that addresses two of the most important authentication aspects: security and user experience. We provide compliant identity authentication, advanced biometrics, and secure credential protection with a mobile app that streamlines onboarding and adoption. It’s easier for you, easier for your users, and hardened against threats like identity theft or biometric spoofing.
BlockID can fulfill these innovative promises through a unique combination of technologies:
- Identity Proofing: BlockID includes Identity Assurance Level 2 (NIST 800-63A IAL2), detects fraudulent or duplicate identities, and establishes or reestablishes credential verification.
- Identity-Based Authentication Orchestration: We push biometrics and authentication into a new “who you are” paradigm. BlockID uses biometrics to identify individuals, not devices, through identity credential triangulation and validation.
- Integration with Secure MFA: BlockID readily integrates with a standard-based API to operating systems, applications, and MFA infrastructure at AAL2. BlockID is also FIDO2 certified, protecting against attacks that attempt to circumvent multi-factor authentication.
- Cloud-Native Architecture: Flexible and scalable cloud architecture makes it simple to build applications using our standard API, including private blockchains.
- Privacy by Design: 1Kosmos protects personally identifiable information (PII) in a private blockchain and encrypts digital identities in secure enclaves only accessible through advanced biometric verification.
If you’re interested in learning more about solid and reliable authentication that’s meeting the challenges of tomorrow right now, then catch our webinar on Authentication: Hope-Based vs. Identity-Based. Also, make sure to sign up for our newsletter to stay ahead of 1Kosmos news and updates.
