User Provisioning: The Key to Unlocking Seamless Workflow
Introduction
The digital transformation sweeping across the business landscape has made efficiency and security two sides of the same coin. User provisioning stands at this crossroads, orchestrating both aspects seamlessly. But what is it, and why should organizations care? In this article, we navigate the intricacies of user provisioning and underscore its pivotal role in today’s enterprise ecosystem.
Key Takeaways
- User Provisioning as a Business Enabler: Efficient user provisioning boosts operational efficiency, security, and employee morale. It accelerates the onboarding process, safeguards sensitive data, and sets a positive tone for new hires, increasing productivity.
- The Importance of Continuous Oversight: Regular audits of access rights and systematic de-provisioning for departing employees are essential. This ensures maintained security, compliance, and seamless business continuity.
Understanding the Basics of User Provisioning
User provisioning can be seen as the backbone of user access management. It involves creating, updating, managing, and even terminating user accounts in systems and applications. This intricate process plays a vital role in Identity and Access Management (IAM) – a broader perspective that ensures people access only what they’re permitted to at the proper intervals.
Contrary to popular belief, user provisioning isn’t just about granting access. De-provisioning, or stripping users of specific rights and access when no longer necessary, is equally crucial. This ensures that former employees or those changing roles do not retain undue access, guarding against potential vulnerabilities.
Benefits of Effective User Provisioning
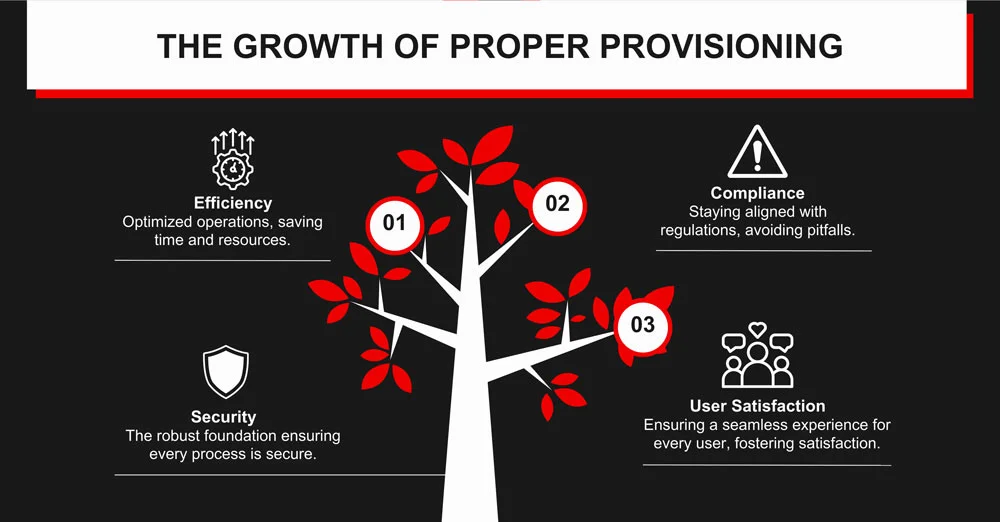
Delving into user provisioning reveals more than just managing access; it’s a gateway to reshaping organizational dynamics. Here are the ways effective provisioning impacts an organization:
- Streamlined Onboarding: An efficient provisioning system means quicker integration for new employees. Instead of waiting for days or even weeks, new team members can get started almost immediately. This enhances productivity and improves the overall employee experience, setting a positive tone from day one.
- Enhanced Security: Security remains a top concern for enterprises, and rightly so. User provisioning mitigates risks by ensuring that only the right people can access the right resources. This proactive approach can deter internal breaches and ensure that sensitive data remains well-guarded.
- Improved Compliance: Compliance standards, often seen as cumbersome, become more manageable with systematic user provisioning. Whether GDPR, HIPAA, or any other regulation, streamlined access management ensures that audits are smooth and violations are rare.
- Reduced Human Errors: Automating user provisioning drastically reduces manual errors. These errors, often overlooked, can be costly in terms of both time and potential security breaches.
- Optimal Resource Utilization: When IT teams aren’t swamped with access requests or troubleshooting access issues, they can divert their energy to more strategic tasks. This optimization can drive innovation and keep organizations ahead in the competitive curve.
With these benefits in mind, it’s worthwhile to delve deeper into the mechanisms and components that make such provisioning possible.
Components of User Provisioning
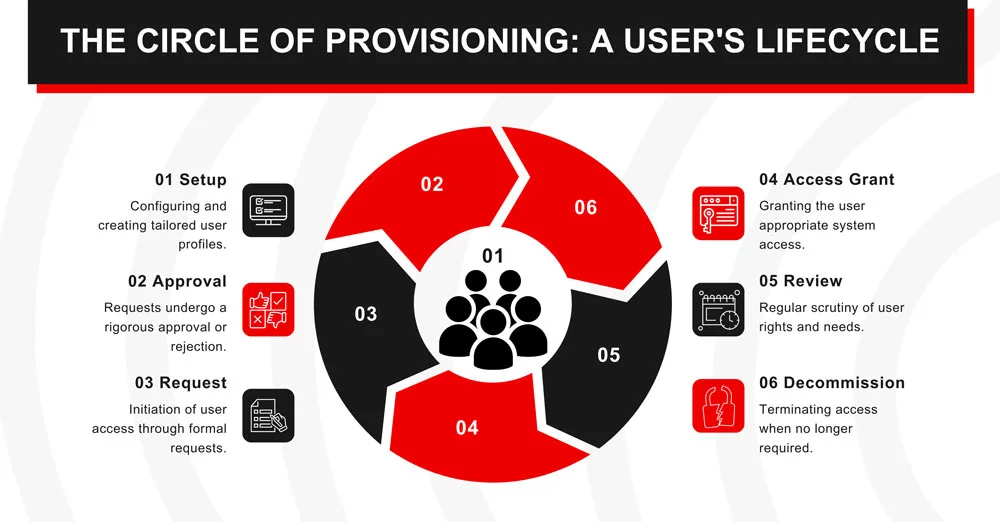
User provisioning is an intricate system of interconnected parts. To grasp its full breadth, let’s explore these essential components:
- Provisioning Policies and Rules: These aren’t mere guidelines but the foundational principles of user provisioning. They determine the criteria for granting or revoking access, ensuring a standardized approach.
- User Roles and Entitlements: The focus shifts to organizational hierarchy and job functions. By categorizing access based on roles (like manager or analyst), it ensures that users only access what’s relevant to their job function, nothing more, nothing less.
- Connectors: These technical integrations allow user provisioning systems to communicate with other applications and platforms. Whether cloud services, internal databases, or third-party apps, connectors ensure seamless data flow and user management.
- Approval Workflows: Not all access requests are granted automatically. Some require managerial or departmental approval. An integrated workflow ensures these requests don’t get stuck in limbo and are either approved or denied promptly.
- Notification Systems: Keeping users and IT teams in the loop is essential. Whether it’s an approved request, a revoked access, or a pending verification, timely notifications ensure transparency and prompt action.
The Role of Automation in User Provisioning
Automation isn’t just a tool; it’s a game-changer in the world of user provisioning. Delving into its role, we can uncover the transformative effects of automation:
- Simplifying Tasks: Routine tasks, when automated, free up valuable time. It ensures that provisioning happens in real-time, reducing latency and enhancing productivity.
- Benefits of Automated Provisioning: Beyond mere time-saving, automation brings consistency, efficiency, and scalability. It ensures uniformity in how access is managed across the organization, regardless of size or complexity.
- Popular Tools: With the rise of digital transformation, numerous tools have sprung up, offering robust provisioning capabilities. These tools, tailored for diverse organizational needs, provide comprehensive solutions that make user provisioning more efficient and less error-prone.
Role-based Access Control in User Provisioning:
The nexus between roles and access rights defines a paradigm where security and functionality converge. To understand its transformative nature, let’s explore Role-Based Access Control in the landscape of user provisioning:
Defining Role-based Access Control (RBAC):
RBAC is a method where permissions are associated with specific roles rather than individual users. When a user is assigned to a role, they inherit the permissions that come with it. This methodology streamlines administrative tasks and reinforces the principle of least privilege.
The Alignment with User Provisioning:
RBAC is invaluable within the context of user provisioning. As organizations scale, manually assigning permissions to every new hire becomes untenable. With RBAC, predefined roles assigned during the provisioning process automatically dictate access levels, ensuring security without compromising efficiency.
Beyond general automation benefits, there’s a specific area worth exploring: the automated assignment of permissions and its profound advantages.
The Advantages of Automated Permission Assignment:
Eliminating Human Error:
Manual processes, by their very nature, are prone to errors. Oversights can lead to security vulnerabilities or operational inefficiencies. Automated permission assignment addresses these risks by consistently applying access rights according to predefined criteria.
Staying Current with Dynamic Roles:
In agile business environments, roles can be fluid. An employee might start in marketing and transition to sales within months. Automated permission assignment ensures that access rights remain relevant, secure, and efficient as these roles evolve.
Challenges in User Provisioning
Even the best systems face obstacles, and user provisioning is no stranger to challenges. As we dive deeper, here are some hurdles that need attention:
- Complex IT Environments: Larger organizations or those undergoing mergers face a labyrinth of systems and applications. This complexity can make provisioning a daunting task, demanding more sophisticated solutions.
- Changing Business Needs: Business dynamics shift. Whether it’s a new department, a change in hierarchy, or the adoption of new technology, user provisioning systems must be agile enough to adapt without hiccups.
- Continuous Compliance: As governments and industries tighten regulations, staying compliant is an ongoing challenge. User provisioning systems must be updated regularly to accommodate these evolving standards.
- Balancing Usability and Security: The tug-of-war between security and ease of use is accurate. Too tight a system can impede operations, while a lax one can open up vulnerabilities. Striking the right balance is crucial.
While these challenges are significant, adopting a set of best practices can act as a shield, guiding organizations toward success in user provisioning.
Addressing Employee Departures: The Imperative of Deprovisioning:
Employee transitions, while natural, bring to light crucial concerns in the realm of access management. Diving into this topic, we uncover the imperatives and nuances of deprovisioning:
Potential Risks of Neglect:
Unchecked access post-departure can have severe consequences. Beyond obvious security concerns, there’s a risk of non-compliance with regulations that mandate timely revocation of access. Furthermore, lingering access can lead to data breaches, either maliciously by disgruntled former employees or inadvertently.
The Process of Systematic Deprovisioning:
Deprovisioning is a multi-step process that involves more than just turning off access. It starts with an exit checklist, followed by the actual revocation of access across all systems. Then, a review ensures that no residual permissions linger. Additionally, critical roles and responsibilities held by the departing employee must be reassigned to ensure business continuity.
Best Practices for Implementing User Provisioning
The journey of user provisioning is one of continual refinement. And anchoring this journey are the best practices that illuminate the path to both security and efficiency:
- Regular Audits and Reviews: Periodically reviewing access rights can unearth anomalies. Whether it’s a user with excessive rights or outdated access, regular checks ensure a clean slate.
- Clear Policies and Procedures: Ambiguity can be a system’s downfall. Clear, documented procedures ensure everyone knows the drill, from IT teams to end-users.
- User Education: While systems do the heavy lifting, users are the first line of defense. Educating them about the importance of security and best practices can prevent inadvertent breaches.
- Integration with Current IT Infrastructure: The best provisioning system fits seamlessly with existing setups, enhancing capabilities rather than adding friction.
- Documentation: Documentation isn’t just bureaucratic red tape. It’s a vital record that tracks changes and reasons for access and provides a reference point during audits or reviews.
With these guidelines, organizations stand poised to make the most of user provisioning, ensuring a harmonious blend of security and operational ease.
Constructing a Business Case for User Provisioning:
Beyond its technical dimensions, user provisioning speaks a language that resonates with business outcomes. To discern its broader implications, let’s dissect the business case for this pivotal process:
Beyond Just Security:
User provisioning isn’t just a security protocol; it’s a business enabler. Beyond safeguarding assets, it streamlines IT operations, reduces overheads, and accelerates onboarding. Each of these factors translates to tangible cost savings and operational efficiencies.
Enhancing Productivity and Morale:
An indirect yet pronounced benefit of efficient user provisioning on employee morale exists. Their productivity soars when staff can access the necessary tools and data without bureaucratic delays. Furthermore, a smooth onboarding experience, free from access-related hiccups, sets a positive tone for their tenure.
Conclusion
Throughout our discussion, we’ve highlighted how user provisioning reshapes how organizations approach efficiency and security. The next step in this evolution is embracing tools that further enhance these strategies. If you’re curious about how BlockID can complement and uplift your existing approach, book a call with our team today.
