Uber Hack: MFA Can’t Fix the Problem Until We Fix MFA
As the teenager taking credit for last week’s Uber hack so ably demonstrated, threat actors have found an unlikely accomplice in multifactor authentication. But how did cyberattackers manipulate MFA instead of getting thwarted by it? And what can be done to stop this from happening again?
As it turns out, the problem isn’t that the ridesharing giant didn’t have MFA in place. The larger problem is that it wasn’t the right type. To understand what I mean, let’s start with the attack itself.
‘Push’ Panic: Ambushed by MFA Requests
Call it MFA Fatigue, MFA Push Attack, Notification Numbness, or Authentication Exhaustion. By whatever name, the Uber hack followed what has become a well-worn tactic in countless corporate breaches. Based on the reporting so far at least, the hacker claims to have stolen an employee’s password and then bypassed the system’s MFA challenge by repeatedly sending push requests to the employee, who seems to have eventually accepted.
The attacker reportedly used this access to infiltrate Uber’s VPN, where they then sent push notifications as if they were the employee, granting themselves persistent access to Uber’s systems. Eventually, they gained entry to a share drive that contained PowerShell scripts, from which they pilfered admin credentials to Uber’s privileged access management (PAM) service.
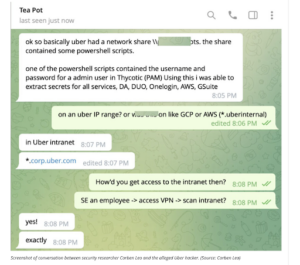
We’re talking serious Kid-in-a-Candy-Store territory here—where the treats (i.e., corporate secrets) come in packages marked G-Suite, VMware, Duo, AWS, and Slack. According to SecurityBoulevard.com, it even included IdP, the company’s OneLogin Identity Provider.
In this instance, defeating MFA doesn’t appear to have required malware, man-in-the-middle attacks, or other technical measures. Instead, the attacker, who’s said to lead the Lapses$ cybercrime group, leveraged sly social engineering tactics. But to be clear, Uber is hardly alone. Recent attacks targeting Okta, Twitter, Rockstar Games, Mailchimp, Robinhood and others employed similar techniques.
But it doesn’t have to be this way.
Fixing MFA: From Here to Identity
The problem is with MFA itself—at least the kind used by most organizations.
While once upon a time usernames and passwords kept corporate secrets secure, they long ago became easy pickings through phishing attacks, spyware, and breach-fueled dark web marketplaces. MFA was meant to solve that by adding at least one other factor to authentication. For a time, that involved a one-time passcode (OTP) sent to the authorized user’s mobile device to confirm they were attempting to access corporate systems.
But cybercriminals learned how to combine tactics that capture not just usernames and passwords into phishing sites but also any OTPs sent as part of the authentication process. The next best step was to send the user a notification about an attempted login, allowing the legitimate user to acknowledge it was, in fact, them logging in. For far too many organizations, that hasn’t ended well.
The problem: Most forms of MFA have been built around a device, instead of the identity of the person using the device. By contrast, next-gen MFA solutions that leverage FIDO2 and NIST 800-63-3 standards use biometric markers tied to a registered smartphone to provide reliable, identity-based authentication that’s impervious to impersonation and account takeover.
Proof of Liveness—Moving Beyond Device-Level Access
With our own next-gen MFA solution, for instance, the device becomes the possession element (what you have), while a live facial scan becomes the inherence element (what you are). To access a network, a system, or an account, a live facial scan is performed to confirm the person attempting to login is in fact the authorized user. No OTPs or push notifications required. In fact, no usernames or passwords required, either.
Not only does 1Kosmos prevent account takeover, it can also be strengthened by learning the user behind the device by scanning a driver’s license, passport, or another form of government-issued identification to verify the identity at every access attempt—preventing unauthorized account access and fraudulent enrollment. An attack like the one that compromised Uber’s systems and those of so many other companies becomes impossible if the authentication request is initiated by the user and verified by their live biometrics.
To prevent the next Uber hack, all entry points within an environment must be managed by a system where user access is tied to the user, rather than to a device. 1Kosmos solutions deliver this. In fact, it’s the first and only NIST-, FIDO2-, and iBeta biometrics-certified platform on the market. And it’s used to perform millions of authentications daily for some of the world’s largest banks, telecommunications, and healthcare organizations.
To learn more about how next-gen MFA can help your organization prevent an Uber-like hack, watch our on-demand webinar,” MFA Tried to Fix Passwords, But How Do We Fix MFA?” now.
