Understanding Smart Card Authentication
Have you ever wondered how a small piece of plastic could be your key to enhanced security and operational efficiency? This article dives into the intricacies of smart card technology, a robust solution in an era increasingly plagued by security breaches and data leaks. You’ll understand what intelligent cards are, how they function, and why their advanced authentication methods are becoming indispensable in various sectors. By the end of this read, you’ll be well-equipped to make informed decisions on integrating this technology into your security infrastructure.
Basics of Smart Cards
What is a Smart Card?
A smart card is a physical card that contains an embedded integrated circuit or chip. This chip can be either a secure microcontroller or an equivalent intelligent device with internal memory or microprocessor components.
Smart cards are often used for personal identification numbers, authentication, data storage, and other applications like secure transactions. They can communicate with readers through direct physical contact or remote connections using contactless radio frequency (RFID) technology.
The utility of smart cards extends across multiple sectors, including banking, healthcare, transportation, and secure access control systems. These cards serve as a secure, portable platform that can perform various functions depending on the programmed data and the applications in which they are used.
Types of Smart Cards
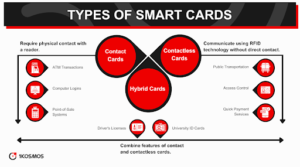
There are generally three types of smart cards: contact cards, contactless cards, and hybrid cards. Contact intelligent cards require physical contact with a reader to function. They are commonly used in ATM transactions, secure computer logins, and point-of-sale systems.
On the other hand, contactless hybrid intelligent cards or cards use radio frequency to communicate with the card reader without direct contact. These are often used in public transportation, access control, and quick payment services.
Hybrid cards combine features of both contact and contactless cards. They contain two chips, one for contact operations and another for contactless operations, providing versatility to the user and the systems they interact with.
They are often used in multifunctional systems that require both types of functionality, such as a driver’s license or university ID card that also serves as a payment and access control card.
Components of a Smart Card
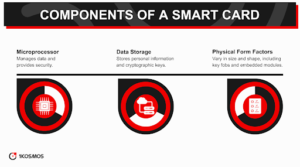
Smart cards typically have a microprocessor or memory chip embedded in a plastic card. The chip has an operating system that manages data and provides security features, including cryptographic algorithms.
Smart cards also possess a storage area for data, including personal information, cryptographic keys, or funds for transactional purposes.
The physical form factor of the card can vary. Standard size resembles a typical credit card but can come in other shapes and sizes, such as key fobs, private keys, or even embedded modules in smartphones.
Depending on the card type, the interface may be exposed to electrical contacts, an embedded antenna for contactless communication, or both.
How Smart Card Authentication Works
Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates.
The chip can generate or store authentication data through cryptographic algorithms that a reader can verify. This approach makes the authentication process for debit cards highly secure and reduces the risk of fraud or unauthorized access.
The Authentication Process Explained
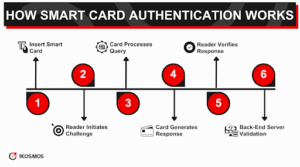
When a smart card is inserted into a reader or a competent card certificate brought within the proximity of a contactless reader, the reader initiates a challenge-response mechanism. First, the reader queries the card for specific information.
The card’s chip then processes this query and generates a response using its information stored in cryptographic keys. To confirm the card’s authenticity, the reader verifies this response against its data.
A back-end server might be involved in more advanced systems to validate the transaction further. This multi-step verification ensures that even if someone gains physical access to a user account or a debit card, it is tough to forge or manipulate the authentication process.
Common Protocols and Technologies
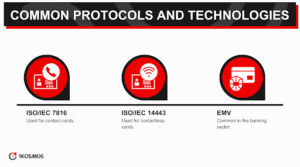
Smart cards often use standard protocols such as ISO/IEC 7816 for contact cards and ISO/IEC 14443 for contactless cards. Other technologies like EMV (Europay, MasterCard, Visa) are popular in the banking sector for secure transactions.
These protocols and technologies govern the physical characteristics, radio frequencies, and data transmission between the intelligent card reader and the reader.
Different sectors might have specialized protocols or custom configurations to make magnetic stripe cards meet specific security or functional requirements.
However, adherence to globally accepted standards ensures interoperability and wider acceptance of the smart card technology.
Benefits of Smart Card Authentication

Smart card authentication brings a plethora of advantages to the table. This technology adds sophistication and efficiency to any integrated system, from enhanced security to streamlined operations.
Enhanced Security Features
The most obvious advantage of using smart card technology is the security improvement. The embedded chip in the smart card can securely store cryptographic keys and other sensitive data.
Because the private key and data are stored in a chip rather than a magnetic stripe, it is much more difficult for unauthorized persons to copy or manipulate the data. This adds a strong layer of security against cloning, skimming, and other forms of fraud.
Additionally, the chip can execute complex cryptographic algorithms, allowing for secure communications between the smart card user and the reader. With the integration of multi-factor authentication, smart cards provide users with a robust defense against many security threats.
User Convenience and Efficiency
While intelligent cards offer users high security, they are also incredibly user-friendly. For most applications, users have to tap or insert their cards into a reader, making the process quicker and more streamlined compared to traditional methods like manual entry of passwords or PINs.
This not only enhances user experience but also improves operational efficiency. In a corporate environment, a single smart card security token can serve multiple purposes—such as access control, secure data storage, and even digital certificates and signatures—reducing the number of credentials a user has to manage.
Scalability and Adaptability
Smart cards are highly scalable and can be easily integrated into existing systems. As organizations grow, the smart card system can be expanded without significant changes to the infrastructure.
Moreover, the cards are adaptable to new technologies and can be updated to meet evolving security standards or to add new functionalities.
Challenges and Limitations

Despite its many advantages, smart card technology is not without its drawbacks.
Costs and Budget Constraints
Implementing a smart card system can be expensive initially. The cost includes not just the cards themselves but also the readers and the back-end infrastructure.
While the long-term benefits may justify the costs, budget constraints can be a significant barrier for smaller organizations or projects with limited funding.
Technological Hurdles
Interoperability can be challenging for smart card devices, especially systems requiring multi-vendor collaboration. If not properly planned, this can lead to compatibility issues.
Moreover, older smart card systems may become obsolete as technology advances, requiring upgrades or replacements.
User Training and Acceptance
While smart cards are generally user-friendly, they do require some level of user training. Understanding how to use the cards correctly, what to do in case of loss or theft, and how to manage PINs or other secondary authentication methods are all essential for the practical usage of intelligent health cards. User acceptance can also be a hurdle, particularly for those who are not tech-savvy.
Best Practices for Implementing Smart Card Authentication
Several best practices can guide the process when implementing smart card technology.
Vendor Selection and Compatibility
Choosing the right vendor is crucial for a successful implementation. Look for vendors who adhere to global standards to ensure interoperability and future scalability.
Also, consider the range of products and services offered by smart card vendors, including the availability of updates and customer support.
Software and Hardware Requirements
Before deploying smart cards, thoroughly assess the existing infrastructure to determine what upgrades or changes are needed.
This includes evaluating the software to manage the smart card system and the hardware that supports smart cards, card readers, and servers. Make sure they meet the required security and operational standards.
Ongoing Maintenance and Updates
Once the smart card system is up and running, it will require regular maintenance to ensure it stays secure and functional.
This includes regular software updates, monitoring for unusual activities, and periodic reviews to assess the need for system upgrades or new features.
Implementing smart card authentication can significantly improve both security and efficiency in a wide range of applications.
While there are challenges for smart card users to consider, the benefits of user authentication often outweigh the drawbacks, making smart cards a worthwhile investment for many organizations.
Enhancing Smart Card Authentication with BlockID
1. Biometric-based Authentication: We push biometrics and authentication into a new “who you are” paradigm. BlockID uses biometrics to identify individuals, not devices, through credential triangulation and identity verification.
2. Identity Proofing: BlockID provides tamper evident and trustworthy digital verification of identity – anywhere, anytime and on any device with over 99% accuracy.
3. Privacy by Design: Embedding privacy into the design of our ecosystem is a core principle of 1Kosmos. We protect personally identifiable information in a distributed identity architecture, and the encrypted data is only accessible by the user.
4. Distributed Ledger: 1Kosmos protects personally identifiable information in a private and permissioned blockchain, encrypts digital identities, and is only accessible by the user. The distributed properties ensure no databases to breach or honeypots for hackers to target.
5. Interoperability: BlockID can readily integrate with existing infrastructure through its 50+ out-of-the-box integrations or via API/SDK.
6. Industry Certifications: Certified-to and exceeds requirements of NIST 800-63-3, FIDO2, UK DIATF and iBeta Pad-2 specifications.
To learn more about the 1Kosmos BlockID solution, visit the platform capabilities and feature comparison pages of our website.
