Understanding Step Up Authentication: From Basics to Benefits
Ensuring the safety of sensitive data and privacy shifts from just a priority to an absolute necessity. Authentication, the gatekeeper of these digital resources, is crucial in this fight against cybercrime. In this article, you will learn what it is, why it’s helpful, how it differs from other types of authentication, and how you could implement it in your organization.
What is Step-Up Authentication?
Step Up Authentication is a dynamic form of multi-factor authentication. It works by adjusting the level of security and user verification based on the associated risk of a specific action, transaction, or mobile account.
Different triggers can prompt Step Up Authentication’s activation, like irregular user behavior, access requests from unfamiliar locations or devices, or high-risk transactions accessing sensitive data. Users may initially authenticate via traditional methods (username/password), but Step Up Authentication comes into play as the perceived risk escalates, demanding additional login credentials.
Step Up Authentication uses a hierarchical model adaptive authentication scheme, scaling from simple to complex; it provides the flexibility to apply the optimal level of security based on the perceived threat or the user’s risk profile.
The Anatomy of Step-Up Authentication
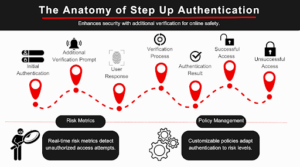
The behind-the-scenes operation of Step Up Authentication is a balance between risk assessment and corresponding adjustments to the step up authentication work up level. Each transaction or request initiates a process where the system evaluates the risk level and prompts the user for a related step up authentication.
To make these decisions, the system utilizes various risk assessment metrics. These include factors such as the sensitivity of the requested data, the location of the user’s location request, the behavior of the user, and even the time of the request.
Policy management plays a big role here, as it sets the rules and parameters for when and how the system should step up the authentication process. These policies, dictated by the nature of the business and its unique security requirements, ensure that the system remains secure and user-friendly.
The Evolution of Authentication
The progression of authentication techniques paints an interesting picture of human ingenuity in the face of evolving threats. Beginning with the humble password, these techniques have developed in response to escalating risks and more sophisticated threat actors.
The initial stage was dominated by password-based authentication systems, a straightforward and user-friendly method, yet not without its weaknesses. Passwords, being susceptible to breaches via techniques like brute-force attacks and phishing, necessitated a more robust system.
Subsequently, security tokens emerged as a new layer of protection. Yet, their physical nature introduced inconvenience and added risk of loss or theft. Later, the advent of biometric authentication marked a significant stride forward against identity theft, tying access to unique human characteristics such as fingerprints or retinal patterns.
The most significant leap in this evolutionary process was the introduction of multi-factor authentication, combining multiple layers of security to create a formidable barrier to unauthorized access to sensitive information.
While both Step-Up Authentication, Multi-Factor Authentication (MFA), and Adaptive Authentication serve the goal of improved security, they differ significantly in their approach.
MFA involves presenting two or more independent credentials at every step up authentication vs. event. This could include something the user knows (password), something the user has (token), or something the user is (biometrics). MFA’s strength lies in its layered defense, using multiple authentication factors and making it challenging for unauthorized users to gain access even if they compromise one aspect.
Adaptive Authentication employs real-time risk assessments, considering many factors such as device reputation, IP reputation, geolocation, and behavior anomalies. Based on these assessments, Adaptive Authentication may permit, or deny authentication apps, or step up the authentication process.
Step-Up Authentication adjusts its various authentication factors and requirements based on the perceived risk level of a transaction or request. It might begin with a simple or two-factor authentication, such as a password, and add more layers as risk escalates. It offers the flexibility of user-friendly authentication for low-risk actions and robust security for higher-risk operations.
Viewing vs. Editing Data
One of the significant features of Step-Up Authentication is its ability to adapt to the nature of the user’s actions. For instance, when a user views data, the authentication process might require only the user’s password or a simple username and password in/password combination. This allows users to perform low-risk actions with minimal friction.
However, when the same user attempts to edit or export sensitive data, the system recognizes the higher risk and steps up the authentication process. This could involve using additional authentication credentials, such as a one-time password, biometric verification, or answering security questions. This dynamic response to requires users based on the action type underlines the adaptability and intelligence of Step-Up Authentication.
Step-Up Authentication in Practice
In practice, you’ll encounter Step Up Authentication in different scenarios, Financial institutions often apply it during high-value transactions. Cloud services employ it when users request access to susceptible information. It’s becoming increasingly ubiquitous across digital platforms, from email services to social media networks.
Sectors like healthcare, finance, education, and corporate entities, utilize Step Up Authentication as an essential tool in their security arsenal. It is increasingly recognized as a powerful means to secure sensitive data, protect user identities and stolen credentials, and maintain system integrity.
Step-Up Authentication Use Cases
Step-Up Authentication is not just a theory but a reality with practical applications across various digital platforms. For example, take a standard action like transferring funds from a banking app. Users might log in to the app using a username/password or biometric authentication. However, when the user initiates a high-value transfer, the system might request additional identity verification as a one-time password (OTP) sent to the user’s registered mobile number or email.
Another use case can be found within corporate systems; an employee may be able to access common, low-sensitivity resources using a simple password. Still, when attempting to access further sensitive resources, more sensitive information, or administrative controls, the system prompts them to undergo further authentication, such as answering security questions or presenting a physical token.
The Strengths of Step-Up Authentication
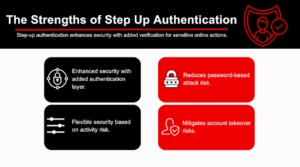
By assessing its impact, the merits of Step Up Authentication become abundantly clear. Its greatest strength lies in its ability to bolster security, creating a robust defense against a wide array of cyber threats.
But its benefits extend beyond security; it contributes significantly to improving user experience, as the need for rigorous additional authentication factors and measures only arises under elevated risk conditions. This reduces friction and potential frustration in day-to-day user interactions.
From a compliance perspective, Step Up Authentication also aids in meeting regulatory requirements for data breach protection. Moreover, it has become a potent tool in the risk management arsenal, offering an adaptive and responsive approach to data breaches and threat mitigation.
Pitfalls and Proactive Measures
Like any system, Step Up Authentication has its potential pitfalls. These include technical implementation challenges, user acceptance, and the ever-present struggle to balance security with ease of use. However, with a strategic approach, these obstacles can be navigated effectively.
Proactive problem-solving measures, such as comprehensive user education programs, policy optimization, and ongoing system monitoring and updating, are key to addressing these challenges.
Security Implications and Concerns in Step-Up Authentication
Though a significant security improvement, step-Up Authentication has potential risks and vulnerabilities. Understanding these security implications and how they can be mitigated is essential to ensure robust protection against cyber threats.
One potential concern is user acceptance and cooperation. Given its nature, users may need clarification on the changing requirements for authentication. This issue is not just a usability concern but also a security concern, as user non-compliance or bypass attempts can introduce vulnerabilities into the system.
Another concern revolves around the accuracy of risk assessment. The effectiveness of Step-Up Authentication depends primarily on correctly identifying and responding to potential risks. Inaccurate risk assessments can lead to security breaches if high-risk actions are not identified correctly and high-risk resources don’t trigger a step-up in authentication.
The additional security measures used in Step-Up Authentication, like biometrics or security questions, bring potential vulnerabilities. For instance, biometric data can be spoofed, and security questions can often be guessed or discovered through social engineering.
Mitigation Practices for Step-Up Authentication
Mitigating these concerns involves several strategies:
- Clear communication about how the system works and its necessity can be beneficial to increase user acceptance.
- User training can also help ensure that users understand the authentication requirements.
- Refinement of the risk assessment algorithm and learning from past mistakes are critical for improving risk assessment accuracy.
- Regular auditing and testing can help identify potential weaknesses in the risk assessment process.
As for the vulnerabilities related to additional security measures, it is key to ensure these are implemented with their own security best practices. For instance, biometric data should be stored securely, and liveness detection tools, like BlockID, should be used to prevent spoofing.
Enhancing Step-Up Authentication with BlockID
BlockID by 1Kosmos enhances the functionality and security measures of Step-Up Authentication by leveraging biometric technology and other features. Its integration forms a robust, user-centric authentication framework ideal for modern digital infrastructures.
- Biometric-based Authentication: We push biometrics and authentication into a new “who you are” paradigm. BlockID uses biometrics to identify individuals, not devices, through credential triangulation and identity verification.
- Identity Proofing: BlockID provides tamper evident and trustworthy digital verification of identity – anywhere, anytime and on any device with over 99% accuracy.
- Privacy by Design: Embedding privacy into the design of our ecosystem is a core principle of 1Kosmos. We protect personally identifiable information in a distributed identity architecture, and the encrypted data is only accessible by the user.
- Distributed Ledger: 1Kosmos protects personally identifiable information in a private and permissioned blockchain, encrypts digital identities, and is only accessible by the user. The distributed properties ensure no databases to breach or honeypots for hackers to target.
- Interoperability: BlockID can readily integrate with existing infrastructure through its 50+ out-of-the-box integrations or via API/SDK.
- Industry Certifications: Certified-to and exceeds requirements of NIST 800-63-3, FIDO2, UKDIATF and iBeta DEA EPCS specifications.
With its adaptable approach, scalable features, and the perfect equilibrium it strikes between security and user experience, Step Up Authentication has become a critical element in contemporary cybersecurity landscapes. Integrating Step Up Authentication might seem daunting, but it’s essential to fortify your security framework. If you’re considering making Step Up Authentication a cornerstone of your security infrastructure and seeking a solution that can effortlessly manage your authentication requirements, don’t hesitate to contact our team today.
