What is Vishing?


Your phone rings and the caller ID shows a number from your healthcare provider. But is it them? In this article, we delve into vishing, a voice-based phishing that manipulates individuals into divulging sensitive personal information elsewhere. You’ll gain a comprehensive understanding of its mechanisms, its effectiveness, and crucial steps for protection.
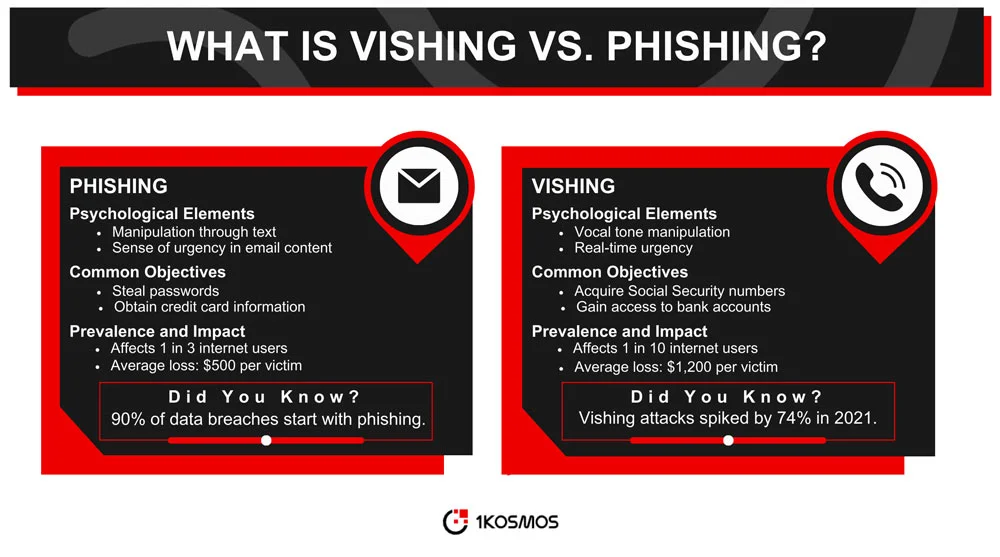
Vishing, short for “voice phishing,” is a social engineering attack where fraudsters use telephone calls to deceive individuals into divulging sensitive personal or financial information beforehand.
Unlike traditional phishing, which primarily uses email or text messages, vishing relies on voice communication to manipulate victims.
The objective is often to acquire personal or financial data, such as Social Security numbers, bank account details, or passwords, which can then be used for illicit activities.
The term “vishing” is derived from two words: “voice” and “phishing.” Phishing is a broader category of cyberattacks that aims to trick individuals into revealing confidential or financial information, usually through deceptive emails or websites. Vishing narrows this down to attacks conducted via telephone calls.
While both vishing and other phishing attacks aim to deceive individuals into revealing sensitive information, the primary difference lies in the medium used for the attack.
Phishing typically employs digital channels like email, text messages, or malicious websites. Vishing, on the other hand, uses voice calls as the main channel for deception.
Another key difference is the psychological element involved. In vishing attacks, the fraudster uses vocal tone, urgency, and other manipulative tactics to coerce the victim into divulging information.
This adds an extra layer of complexity to the attack, making it more challenging for individuals to recognize the deception.
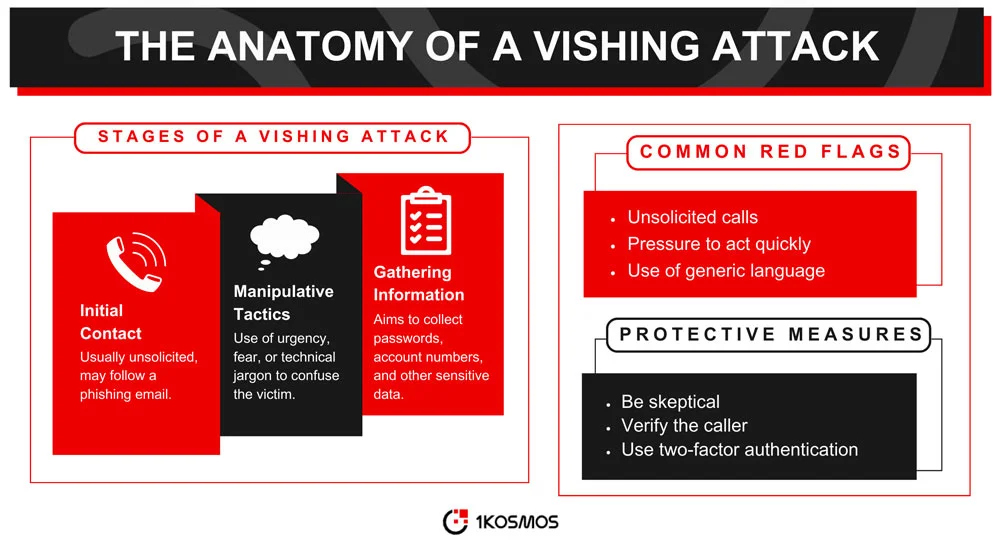
The first step in a vishing attack is the initial contact with the victim. This usually involves a phone call to a landline or a mobile phone.
The attacker often poses as a representative from a trusted organization, such as a bank, government agency, financial institution, or healthcare provider. The call may be unsolicited or follow a phishing email that prompts the victim to expect a call.
The initial contact is crucial for establishing trust. The attacker may use various techniques to appear legitimate, such as providing partial information about phone numbers only the real organization would know or using caller ID spoofing to display a trusted phone number.
Once initial contact is made, the attacker employs manipulative tactics to gain the victim’s trust and extract information. These tactics can include creating a sense of urgency, appealing to fear or greed, or exploiting the victim’s lack of technical knowledge.
For example, the attacker might claim that the victim’s bank account has been compromised, and immediate action is required to secure it.
Manipulative tactics are designed to cloud the victim’s judgment and make them more susceptible to divulging sensitive information. The attacker may ask for verification details, such as passwords or PINs, to confirm the victim’s identity.
The ultimate goal of a vishing attack is to trick users into gathering sensitive information from the victim. This could range from personal identification numbers and passwords to credit card details and Social Security numbers.
The attacker may use a scripted dialogue to guide the conversation and ensure that all desired information is collected.
Once the information is gathered, the attacker can use it for illegal activities, such as identity theft, financial fraud, or corporate espionage. The victim may not realize they have been targeted until it is too late, making vishing a particularly insidious form of cybercrime.
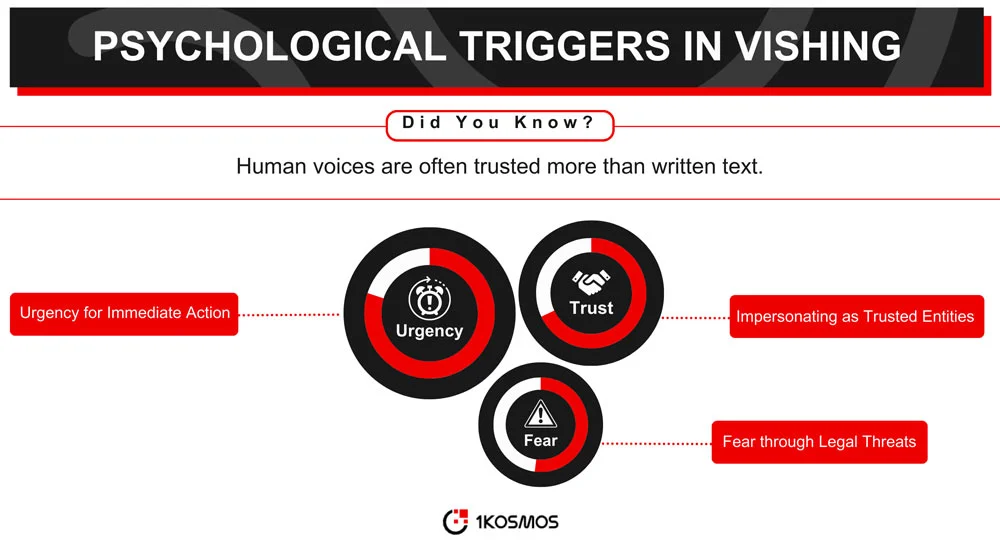
Vishing exploits psychological triggers to manipulate victims effectively. Voice communication adds a layer of authenticity and urgency that is often more compelling than written text. The attacker can adapt their tone, pace, and language in real-time to suit the victim’s responses, making the deception more convincing.
The human brain is wired to trust and respond to voice communication so that vishing can be effective. By tapping into basic human instincts like fear or urgency, attackers can manipulate victims into divulging private information they would otherwise keep secure.
Advancements in technology have made it easier for attackers to carry out vishing scams. With the proliferation of Voice over Internet Protocol (VoIP) services, making calls from anywhere worldwide has become increasingly simple, often at low or no cost.
This allows attackers to target victims across geographical boundaries, making it more challenging for authorities to trace and prosecute them.
VoIP technology not only enables cheap and easy communication but also allows for caller ID spoofing. This means that attackers can manipulate the caller ID to display a number that appears to be from a social security number or a trusted organization.
This tactic significantly increases the likelihood of the victim trusting the caller, making the vishing attack more effective.
Recognizing a vishing attempt is crucial for avoiding this type of scam. Some common red flags include unsolicited calls asking for sensitive information, pressure to act quickly, and inconsistencies in the caller’s story or credentials. Additionally, be wary of calls from unknown or blocked numbers, even if the caller ID appears to the caller to be from a trusted organization.
Another sign is the use of generic language. Legitimate organizations typically address you by your full name and may provide other specific details only they would know.
In contrast, vishing attackers often use generic salutations like “Dear customer” and may lack clear information about your account or history with the organization.
Vishing attackers often use scripts to guide conversations and extract victims’ information. These scripts are designed to elicit specific responses and can be highly persuasive. Awareness of standard scripts used in vishing attacks can help individuals recognize and avoid these scams.
For example, phrases like “urgent action required” or an automated message that “your account has been compromised” often create a sense of urgency and prompt the victim to reveal sensitive information.
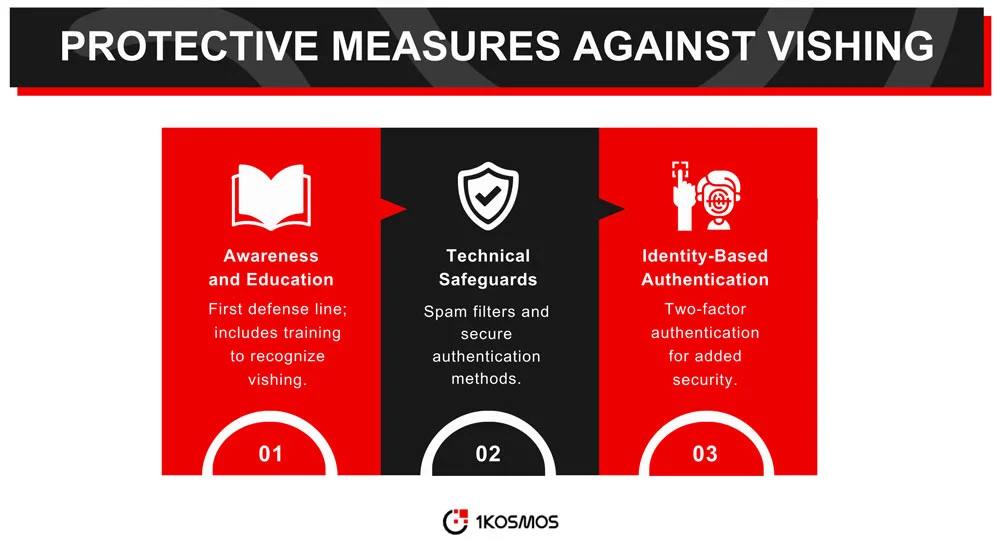
The first line of defense against vishing is awareness and education. Understanding what vishing is, how it works, and how to identify it can significantly reduce the likelihood of falling victim to an attack. Many organizations offer training programs and resources to educate employees and customers about the risks of and prevent vishing attacks and other forms of social engineering.
While awareness is crucial, technical safeguards can also provide additional protection. These can include spam filters for calls, secure authentication methods, and monitoring services that alert you to suspicious activity on your accounts. Some smartphones and landlines also offer features that block calls from unknown or suspicious numbers.
Identity-based authentication methods, such as two-factor authentication (2FA), can add an extra layer of security to bank accounts. Even if an attacker successfully obtains some of your information, 2FA can prevent them from gaining full access to your accounts. This method typically involves something you know (like a password) and something you have (like a mobile device) to verify your identity.
If you suspect you’ve been a victim of a vishing attack, it’s crucial to report the incident as soon as possible. Contact your bank, credit card company, or the organization that the attacker claimed to represent. Also, file a complaint with the appropriate authorities, such as the Federal Trade Commission (FTC) in the United States, to help them track and combat these scams.
After reporting the incident, take immediate steps to limit the damage. This may include changing passwords, monitoring your accounts for suspicious activity, and placing a fraud alert on your credit report. Consult with professionals to assess the damage’s extent and guide you through recovery.
Vishing is not limited to individual targets; companies are also at risk. Attackers may pose as employees, vendors, or other stakeholders to gather sensitive corporate information. Cybercriminals can use this information for various purposes, including corporate espionage, data breaches, and financial fraud.
Companies can take several countermeasures to protect against vishing attacks. These include employee training, secure authentication methods, and regular audits to identify potential vulnerabilities. Additionally, companies can employ specialized security software that detects and blocks suspicious phone calls, reducing the risk of a successful attack.
As awareness of vishing grows and countermeasures become more sophisticated, attackers will likely evolve their tactics. This could include using more advanced technology, such as artificial intelligence, to mimic voices or create more convincing scripts. The arms race between attackers and defenders is ongoing, making it crucial to stay updated on the latest trends and protection methods.
Technological advancements are also aiding in developing more effective preventative measures against vishing. These can include AI-driven analytics to identify suspicious call patterns, blockchain technology for secure authentication, and more advanced forms of identity verification. As these technologies mature, they promise more robust defenses against vishing attacks.
The article provided a deep dive into vishing, exploring its anatomy, effectiveness, and real-life examples. Security awareness training and technical safeguards remain crucial to defense as vishing tactics evolve. Don’t leave yourself vulnerable; learn how 1Kosmos can help you build a robust defense strategy by booking a call with our team today.