Verifiable Credentials: A Deep Dive into Enhanced Identity Assurance


Modern technology has provided us with countless conveniences but has also brought unique challenges, especially in identity verification. As cyber threats grow, establishing a person’s identity online with a high degree of certainty becomes imperative. At the core of this challenge lies the concept of verifiable credentials.
They’re not merely digital equivalents of identity cards or licenses. Instead, they represent a complex intersection of claims, validations, and sources of truth, all bound by rigorous standards like the NIST 800-63-3 guidelines.
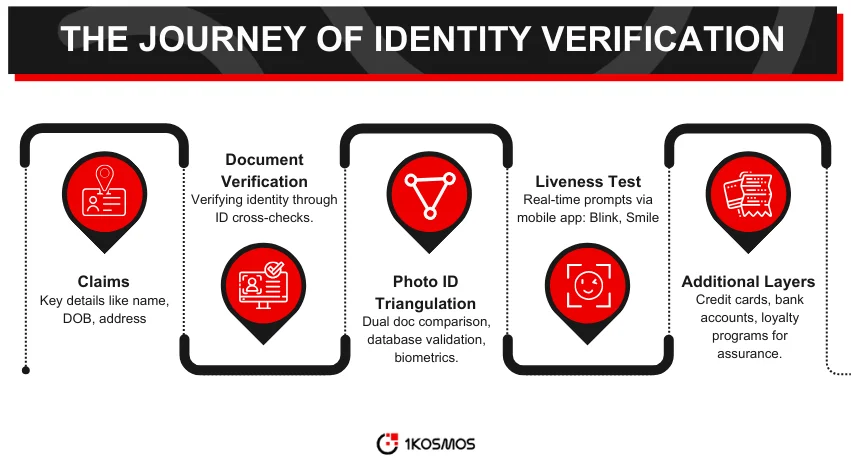
In the realm of identity verification, claims play a pivotal role. They are pieces of information that an entity asserts about itself. For instance, an individual’s full name, date of birth, or residential address are all claims.
The BlockID system utilizes a variety of these claims to authenticate identities. But here’s the catch: a single claim, in isolation, does not guarantee authenticity. This is why claims need to be verified using multiple trustworthy sources.
Documents have long been the primary means of verifying an individual’s identity. These state or bank-issued documents have been the cornerstone of identity verification, from passports to driver’s licenses. These documents serve a foundational role in the process undertaken by BlockID.
They’re used to confirm essential claims such as an individual’s name or date of birth. But as with any system, there are vulnerabilities. Documents can be forged, stolen, or legitimately issued under pretenses.
Photo identification offers a visual means to validate an individual’s claims. But how can one ensure the photo ID is genuine and represents the individual? BlockID approaches this challenge in stages.
Begin with two recognized documents: a passport and a driver’s license. These are cross-verified to ensure they match in terms of names, dates of birth, and photographs. Achieving a match provides an initial validation, leading to an IAL1 score. However, it needs to be more foolproof. What if someone stole both documents?
BlockID then interfaces with official databases to ramp up the verification process. For instance, querying the State Department can validate the authenticity of a passport. Similarly, the AAMVA database can confirm the legitimacy of a driver’s license. Only once a document clears this phase does the system consider progressing to an IAL2 score. But there’s another step.
Biometrics, like fingerprint or facial recognition, offer an advanced level of identity verification. Modern passports come embedded with chips storing biometric data. The BlockID leverages this, but it continues beyond there. It also employs liveness tests through its mobile application. Users are prompted to perform actions, such as blinking or smiling, which are then analyzed in real time. This ensures that not only is the user genuine, but they are also physically present during the verification.
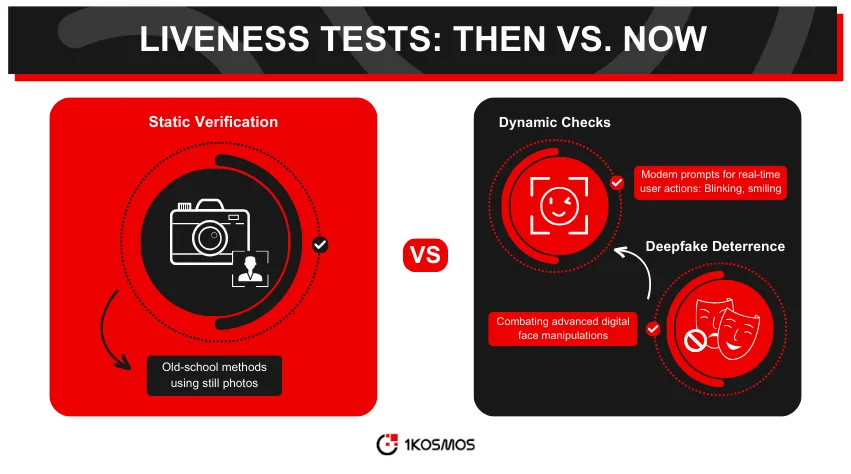
It might sound futuristic, but liveness tests are crucial in the evolving landscape of identity verification. With the growing sophistication of deepfakes and other digital manipulations, static images or stored video clips are no longer reliable.
The BlockID mobile application’s liveness test is a step towards thwarting such advanced threats. By asking users to follow dynamic prompts, the system ensures an actual person is present and not some pre-recorded video or image.
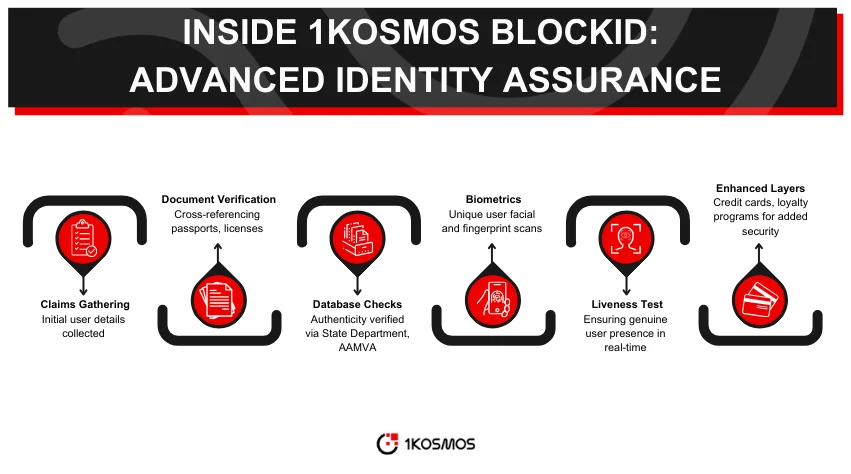
While photo IDs, biometrics, and liveness tests form a strong triad of verification, they aren’t the only tools in the arsenal. Other layers can be added to enhance the assurance of identity verification further. Consider financial instruments like credit cards or direct validations like bank account numbers.
Even details from loyalty programs can serve as auxiliary sources of truth. Combined with the primary methods, these additional sources create a robust framework, ensuring identities are validated with the highest possible assurance.
Identity verification isn’t a static field. As verification techniques evolve, so do the methods of those trying to bypass them. This means systems such as BlockID must remain several steps ahead, constantly innovating and refining their processes.
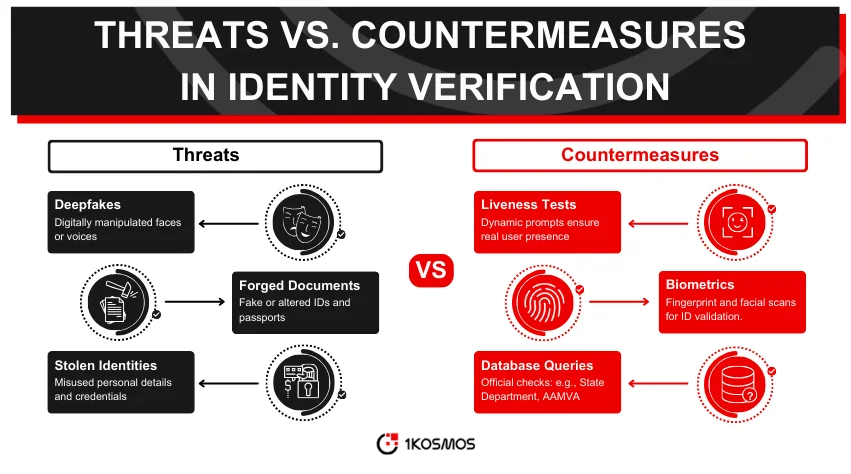
With digital forgeries becoming more sophisticated, new threats emerge. Deepfakes, for instance, can convincingly replace a person’s likeness in videos or photographs. Such advancements demand countermeasures. Liveness tests and dynamic prompts are tools that counter these evolving threats.
No system is infallible. Genuine users might be flagged incorrectly, or a fraudulent attempt might slip through. It’s crucial for identity verification platforms to minimize these errors. Continuous refinement, feedback loops, and adaptive algorithms play a role in reducing such discrepancies.
The National Institute of Standards and Technology (NIST) sets guidelines as a benchmark for identity assurance. Systems like BlockID don’t just aim to meet these guidelines; they strive to exceed them.
This specific guideline from NIST lays the groundwork for digital identity services. It categorizes identity assurance into various levels, each demanding stricter verification protocols. By adhering to and surpassing these guidelines, platforms ensure a standardized, high level of trustworthiness.
Beyond just a mark of quality, compliance with NIST guidelines signifies a commitment to security and reliability. It assures users and stakeholders that the platform they trust with their credentials adheres to internationally recognized standards.
The boundaries between our physical and online identities continue to blur. With this evolution, the importance of reliable, robust, and agile identity verification systems only grows. Systems like BlockID, armed with a multi-faceted approach, are at the forefront of this battle against identity fraud. To see how BlockID can help you improve your security posture, book in a call with our team today.